Access Control System Project Plan
Brian Jerozal
Instructor: Ralph Warren
CIS 210
January 26, 2017
Project Scope Statement
The project of installing an access control system in a dormitory is requirement which is coming from the Board of directors of college. Scope of the project is to develop a system which ensure the authorized access in to the dormitory and record all the activities which are taking place at the door of dormitory in order to identify the potential threat who is trying to get the unauthorized access in to the dormitory. For getting entry, user authentication will be requiring which will take place when register person will use his/her issued identification card against the electronic proximity reader. This project is big step form collage to ensure the security at the campus.
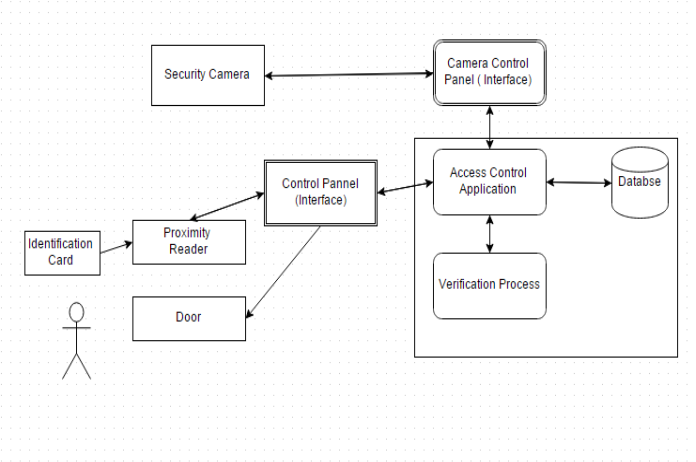
Project goals is to implementing an access control system (ACS) in a dormitory by integrating an electronic proximity reader, application which will handle this device and will do verification of user form created database and the existing security camera who will monitor all the activities and will record them in order to ensure the secure access to the dormitory. Deliverable of this project will be the video footage of dormitory access activity and overall working system. The student or appropriate personnel will have three opportunities to open the entryway if the client neglects to open the entryway on the third endeavor then the alert will go off. The “ACS” will likewise be intended to permit the security chairman to make changed for the “ACS” operations. These progressions will be the camera positions setting the caution time and setting the time the quarters entryways will bolt. The gadget utilizes a reception apparatus curl to control the “RFID” tag implanted in the understudy ID card which peruses the actuate reaction from the card. The reaction is then separated and controlled into helpful information and deciphered by the security program. This procedure cautions the manager PC by means of serial line and hyper term. In the event that the card is perused and it is not in the code database a “red LED flashes” for three seconds. A dedicated team of 5 resources will be assigned for this project. Overall project cost including the hardware devices is $15,000. Total duration of project is 3 weeks. First team has to show an internal demo of this project and then final representation of project will be done in the presence of board members of college at the time of project delivery.
Five Major Task with Subtasks
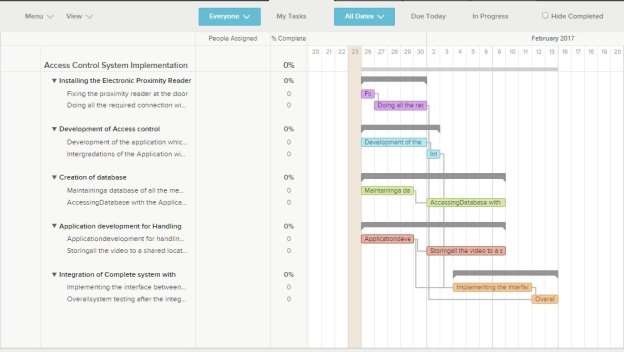
Task 1 – Installing the Electronic Proximity Reader
- Fixing the proximity reader at the door
- Doing all the required connection with the door locks
In this tasks need is to implement physical reader at the door. Requirement is to do all the connection with the door also, so that door can be controller for lock and unlock process.
Task 2 – Development of Access control authorization application
- Development of the application which will do the verification in Java
- Intergradations of the Application with the proximity reader device
Develop an application in java which will be able to fetch from database and will get the identification detail form reader and will match them. On successful match, it will send the information to control panel to unlock the door.
Task 3 – Creation of database
- Maintaining a database of all the members and their identification card
- Accessing Database with the Application
Need is to create a data base of college which will have all the information about identification in the form of relation tables. Add functionality in the application to get the data from Database.
Task 4 – Application development for Handling Security Camera
- Application development for handling camera movement and to handling recording process
- Storing all the video to a shared location which requires secure access
Add functionally to handle the camera and its movement forms the application whenever some user comes at door and uses reader to get entry. Store all the recorded video at particular location
 Task 5 – Integration of Complete system with security camera system
- Implementing the interface between camera and application
- Overall system testing after the integration for complete process
Create interface between panels and integrate the entire component. Test manually complete functionally and video stored by security camera.
Gantt Chart illustrating the project Tasks
System diagram of Application
References
Benantar, M. (2006). Access control systems: security, identity management and trust models. doi: 10.1007/0-387-27716-1
Norman, T. L. (2011). Electronic access control. Retrieved January 26, 2017, from https://books.google.com/books?id=TmRRTfAPfdYC&printsec=frontcover&source=gbs_ge_summary_r&cad=0#v=onepage&q&f=false
Rosenblatt, H. J. (2014). Systems Analysis and Design, 10th Edition. [Strayer University Bookshelf]. Retrieved from https://strayer.vitalsource.com/#/books/9781337003186/