Face Recognition Attendance System 1.1 Introduction
In the 21st century, everything around us has become depends upon technology to make our life much easier. Daily tasks are continuously becoming computerized. Nowadays more people prefer to do their work electronically. To the best of our knowledge, the process of recording students’ attendance at the university is still manual. Lecturers go through manual attendance sheets and signed papers to record attendance. This is slow, inefficient and time consuming. The main objective of this project is to offer system that simplify and automate the process of recording and tracking students’ attendance through face recognition technology. It is biometric technology to identify or verify a person from a digital image or surveillance video. Face recognition is widely used nowadays in different areas such as universities, banks, airports, and offices. We will use preprocessing techniques to detect, recognize and verify the captured faces like Eigenfaces method. We aim to provide a system that will make the attendance process faster and more precisely. The core problem is identified along with solutions and project path. Furthermore, detailed system analysis and design, user interface, methods and the estimated results are presented through our documentation.
Keywords: Attendance; Automate; Recording; biometric; face recognition;
|
FRAS |
Face Recognition Attendance System |
|
NIST |
National Institute of Standards and Technology |
|
UML |
Unified Modeling Language |
|
IDE |
Integrated Development Environment |
|
MS |
Microsoft |
|
VS |
Visual Studio |
|
SQL |
Structured Query Language |
|
SSMS |
SQL Server Management Studio |
|
OO |
Object Oriented |
“Office automation refers to the collective hardware, software and processes that enable automation of the information processing and communication tasks in an organization. It involves using computers and software to digitize, store, process and communicate most routine tasks and processes in a standard office.” [1]
In addition, attendance considered as the biggest issues that may face lecturers in class. It takes time, effort and difficult to manage. Therefore, our project will focus on online student attendance. In another word, the aim of this project is to build a system that help lecturers take students’ attendance in a professional way.
1.2 Problem Definition
Taking and tracking students’ attendance manually, losing attendance sheets, dishonesty, wasted time and high error scales are problems facing the lecturers use the existing attendance system. It is a hard process, take time and cause a lot of paper-based work. As a result, in order to solve these problems and avoid errors we suggest to computerize this process by providing a system that record and manage students’ attendance automatically without needing to lecturers’ interference.
1.3 Project Objectives
Our primary goal is to help the lecturers, improve and organize the process of track and manage student attendance and absenteeism. Additionally, we seek to:
- Provides a valuable attendance service for both teachers and students.
- Reduce manual process errors by provide automated and a reliable attendance system uses face recognition technology.
- Increase privacy and security which student cannot presenting himself or his friend while they are not.
- Produce monthly reports for lecturers.
- Flexibility, Lectures capability of editing attendance records.
- Calculate absenteeism percentage and send reminder messages to students.
1.4 Project Scope
Our project targets the students of different academic levels and faculty members. The main constraint we faced is distinguishing between identical twins. This situation is still a challenge to biometric systems especially facial recognition technology. According to Phillips and his co-researcher paper [2] to get the best results of the algorithms your system employed, they should run under certain conditions for taken pictures (i.e… age, gender, expressions, studio environment…etc.) otherwise, the problem is still ongoing.
They provide application (method) to solve this problem, but in order to use this solution you have to sign a contract with the (NIST) organization and to be a researcher or developer. For us, to solve this issue we suggest to record twins’ attendance manually.
1.5 Contributions of This Study
We have searched for a system that can take, monitor and manage students’ attendance and absenteeism, send reminder messages, calculate absenteeism percentage, and produce weekly, monthly, and annual reports. Based on our searches, there is no integrated system can support our idea.
In this project, we are trying to develop such a system that can do all those tasks. Our project will serve students, lecturers, and the university as whole.
1.6 Project Timeline
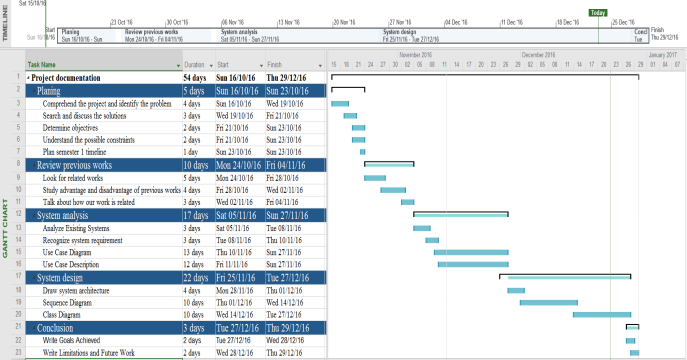 We utilized Gantt chart in figure 1.1, to show a project schedule with the start and finish dates of several tasks of a project and the deadline to submit the project.
We utilized Gantt chart in figure 1.1, to show a project schedule with the start and finish dates of several tasks of a project and the deadline to submit the project.
1.7 Document Organization
This project consists of six chapters. These chapters organized to reflect the scientific steps toward our main objective. A brief description about the contents of each chapter given in the following paragraphs:
- Chapter 1 introduces the problem definition, project objectives, the contribution of this project, the scope of the work, and the project layout.
- Chapter 2 provides the reader with an overview of the literature review.
- Chapter 3 displays the analysis of the existing system, requirements elicitation which includes (functional requirements, nonfunctional requirements, User Requirements.), requirements specification, research methodology.
- Chapter 4 displays the architectural design, object oriented design figure.
- Chapter 6 displays the conclusion that includes limitation and future work.
2.1 Introduction
Over the past decade, taking down students’ attendance process had been developed and changed.The driven force of this development is the desire to automate, facilitate, speed up and save time and efforts. Although that the attendance systems are around us everywhere, Taibah university lecturers still use a traditional way to record students’ attendance either through calling out students’ names or through a passing attendance sheet among students to sign beside their names. Both ways are time consuming and associated with high error scales. In this project, we attempt to reduce wasted time, eliminate buddy clocking, and automate the process. Our system uses facial recognition technology to record the attendance through a high resolution digital camera that detects and recognizes faces and compare the recognize faces with students’ faces images stored in faces database.
Once the recognized face matches a stored image, attendance is marked in attendance database for that person. The process will repeat if there are missed faces. For example, if there are 4 faces missed for a bad position while the detecting phase, then this phase will start again to detect the missed faces and recognize them and continue the attending process. By the end of the month, a monthly report is send to the lecturer contains attendance and absence rates as a chart and the names of absentees. Also, a warning message sends to the student if he passes the allowed number of absence.
In this chapter, we present a brief overview of face recognition in the background section, relevant works to our project with their advantages and disadvantages, how we relate to these studies and how this project can provide some beneficial features for lecturer.
2.2 Background
Most lecturers have a significant number of students and it is hard to keep taking or tracking all their absence. Facial recognition is commonly used in many institutions to take attendance of a significant number of students. There are many errors that could occur during this process, including misidentification and self-recognition [3]. Lecturer can control the errors and correct it.
In the next subsection, brief overview of the usage,techniques, and methods in facial recognition.
2.2.1 Face Recognition Usage
“Face recognition rises from the moment that machine started to become more and more intelligent and had the advance of fill in, correct or help the lack of human abilities and senses.” [4]. Common uses ofFacial recognition clarify in following points;
- Security; can be crime-fighting it will recognize people based on their eyes, nose and face.
- Searching for lost people.
- Games
- Taking student or employee attendance
2.2.2 Face Recognition Techniques and Methods
” Many factors influence the process of face recognition such as shape, size, pose, occlusion, and illumination. Facial recognition, have two different applications: basic and advanced “. Major face recognition recognizes faces or no faces such as balls and animals. If it is a face, then the system searches for eyes, a nose, and a mouth. Advanced facial recognition manages the question on a specific face. This contains unique landmarks: “the width of nose, wideness of the eyes, the depth and angle of the jaw, the height of cheekbones, and the separation between the eyes, and makes a unique numerical code.”
Utilizing these numerical codes, the system then matches that image with another image and distinguishes how comparable the pictures are to each other. The image provenance for face recognition include pre-existing pictures from various databases and video camera signals. [5]
A facial recognition system involves the following phases: Face detection, feature extraction, and face recognition as illustrated in Figure 2.1. [5]
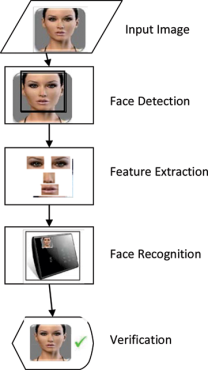
Figure 2.1:General structure of the face recognition system.
The following table compares some of the biometric technology used lately.
Table 2.1: Comparison among some of the biometric technologies
|
Biometric Technology |
Accuracy |
Price |
Tools required |
|
Facial recognition |
Moderate |
Moderate |
Camera |
|
Voice recognition |
Moderate |
Moderate |
Microphone |
|
Fingerprint |
High |
Moderate |
Scanner |
2.3 Related Work
In this section, we highlight some related works that were developed to recognize faces and takedown attendance together with the advantages and disadvantages of each system.
2.3.1 Review of Relevant Work
2.3.1.1 Auto Attendance Using Face Recognition (by Mahvish & Tania)
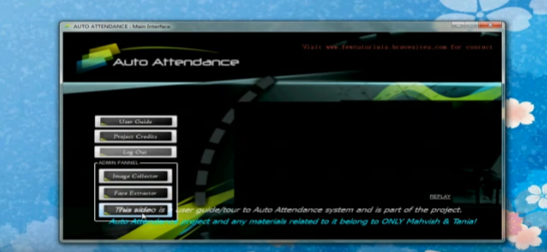
Figure 2.2: Screenshot of Main Interface (Admin Tasks Interface)
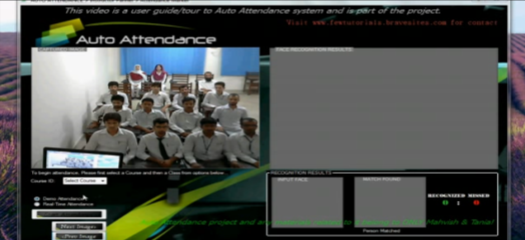
Figure 2.3: Screenshot of Auto Attendance system’s interface
In this project, we have two users responsible for the system [6]. The instructor who takes the attendance and admin who is responsible for managing students’ faces in the face’s database. Admin selects a camera to capture, collect and save images to database or a folder. After the collection and saving the process done the trainingSet manager start to extract faces from the image by face detection.
Finally, the trainingSet manager (Admin) will add the extracted image -person- to class or trainingSet. And as you can see in the illustrated figure, 2.3 above, attendance is taken down by recognizing the faces through a web camera and automatically marked in attendance sheet with daytime. The instructor chooses the course ID and the class ID to begin the attending process.
- Advantages:
- The system stores the faces that are detected and automatically marks attendance.
- Provide authorized access.
- Ease of use.
- Multiple face detection.
- Provide methods to maximize the number of extracted faces from an image.
- Disadvantages:
- The accuracy of the system is not 100%.
- Face detection and loading training data processes just a little bit slow.
- The instructor and trainingSet manager still have to do some work manually.
2.3.1.2 Attendance System on Face Detection (By NevonProjects)
The system is created for employing a simple and a secure way of recording attendance. First of all, the software takes a picture of all the authorized individuals and stores the information into the system’s database. Then, the system stores pictures by mapping it into a face match structure. The system will recognize the registered person and mark his/her attendance along with the arrival time whenever he/she enters the locations again [7].
- Advantages:
- The system stores the faces that are detected and automatically marks attendance.
- Ease of use.
- Manipulate and recognize the faces in real time using live video data.
- Multiple face detection.
- Multipurpose software.
- Can be used in different places.
- Disadvantages:
- The accuracy of the system is not 100%.
- It can only detect face from a limited distance.
- It cannot repeat live video to recognize missed faces.
2.3.1.3 Face Login
“Face Login allows you to log in to your PC by looking at your webcam. FaceLogin associates user accounts with a picture, and then, when looking at your webcam, you can login because it detects you on the webcam”. [8]
- Advantages:
- Only an administrator can run FaceLogin and change its settings.
- More than one way to configure users.
- Can store more than one image for a user to maximize face detection.
- Disadvantages:
- Application’s accuracy is not 100%.
- Adding users manually.
- Associated risks with stored data and images.
- Uses traditional way to access the application.
- Limited use.
2.3.1.4 Biometric Face Detection Attendance Systems
Face recognition systems with time attendance provide multi-biometric and multi-authentication modes. Attached with high resolution infra-red camera works in low light, best face recognition algorithms and identification methods.
Advantages
- Convenient.
- Provide many recognition ways.
- High accuracy.
- Used for secure purposes.
- Provide many communication models.
Disadvantages
- Limited capacity.
- Detect faces from a limited distance.
- People stand in a queue to take their attendance.
- Screen size.
- Still uses traditional authentication PIN way.
2.3.1.5 C-400 Facial Recognition Clocking System
Facial recognition timing systems will give you precise attendance information and stop employees’ buddy clocking – when employee sing on behalf of his colleague-. [9]
Advantages
- C-400 Face recognition timing technology reduces any likelihood of your employees signing for each other in/out.
- Complete suite of reports.
- Printable attendance register in the event of an emergency.
Disadvantages
- There is no External Bell Attachment.
- Device is expensive.
- The face has to be in front of the device to record attendance.

2.3.1.6 Churchix Face Recognition Software
Churchix presents face recognition software, which takes someone’s face through a picture or video and then identifies it by comparing it with those in a database of pictures. The software is becoming more common in every day interactions. [10]
Advantages:
- Attending members in videos and photos.
- High quality photos.
- High accuracy.
Disadvantages:
- Some people they see as a threat to privacy.
- Inability to capture all the faces in the video.
- Restart the video several times to capture all faces.
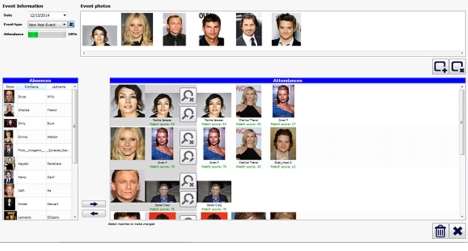
Figure 2.5: Screenshot of Churchix Face Recognition Software
2.3.2 Relationship Between the Relevant Work and Our Own Work
Table 2.2: Comparison among applications viewed in the previous section
|
Application |
Auto Attendance Using Face Recognition by: Mahvish&Tania |
Attendance System on Face Detection By: NevonProjects |
Face Login |
Biometric Face Detection Attendance Systems |
C-400 Facial Recognition Clocking System |
Churchix Face Recognition Software |
Face Recognition Attendance System |
||
|
Database |
√ |
√ |
√ |
√ |
√ |
√ |
√ |
||
|
Hardware |
PC Webcam |
PC , camera |
Pc , webcam |
Camera |
camera |
PC , camera |
PC , camera |
||
|
Language |
C# |
C# |
unknown |
Unknown |
unknown |
unknown |
C# |
||
|
Scope |
student |
student |
anyone |
employees |
employees |
anyone |
Student |
||
|
light-on when-the camera starts |
√ |
||||||||
|
|
√ |
√ |
√ |
||||||
|
unlimited distance |
√ |
||||||||
|
High accuracy |
√ |
√ |
√ |
√ |
|||||
From table 2.2, the main point in our project is to create a system that facilitates students attending process. The following points summarize features will be adopted in the system:
- The light on when the camera starts facial recognition because reduce the error
- There are screen next to the camera to display the result of attendees and absentees
- The system at the end of the class update attendance sheet
2.4 Summary
An automatic attendance management system is needed tool for huge organizations. Many organizations have been used face recognition system such as train stations, airports, and companies. Overall, this chapter provided an overview of some related works that were developed with their advantages and disadvantages. Moreover, we compare between the relevant work and our own work and show the differentiation between them.
The matter that has to be taken into consideration in the future is a method to guarantee users’ privacy. Whenever an image is stored on servers, it must be impossible for unauthorized person to get or see that image.
3.1 Introduction
This chapter examines the analysis that determined the adequacy of the existing attendance system and identifies the requirements of the new system. Additionally, a specification of functional, nonfunctional and user requirements will be presented to understand how the system will work. In the term of analyzing these requirements, UML diagrams of the new system will be presented.
3.2 Analysis of Existing Systems
In the school, colleges and universities attendance system are used to keep the record of a student presence and absence. It is true that the Taibah University has an electronic system but still needs a manual intervention.
There are two case to attend students:
- First, add students’ attendance directly to the attendance web page.
- Second, write attendees’ names on a paper then move it to the web page.
These two cases have drawbacks such as in the first case, there is a possibility to disconnect the connection and chose the wrong date. In the second case, there is a chance to loss the paper and it is a waste of resources We did a questionnaire that was targeted a lecturer in Taibah University and the number of participants nineteen.
The aim of this questionnaire is to determine the satisfaction of the current system. Here are some questions and their statistics.
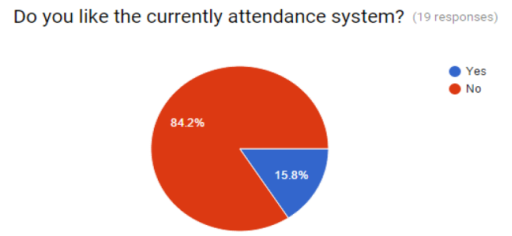
As shown in figure 3.1, 84.2% of lecturers do not like the existing systems, we should take into consideration this percentage and develop a new attendance system.
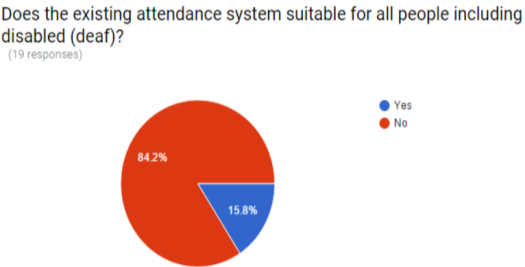
As can be seen from the Figure 3.2, 84.2% of the lecturer sees the existing system not suitable for all people like deaf. This is one of the drawbacks of the existing system, and there are more such as:
- There is always a chance of forgery (one person signing the presence of the other one)
- More manpower is required (some person to take attendance)
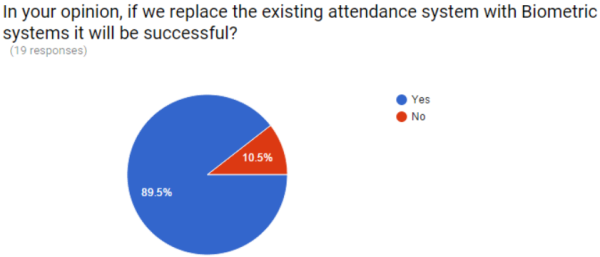 To overcome the problems in the existing system, we will develop a face recognition attendance system.
To overcome the problems in the existing system, we will develop a face recognition attendance system.
The majority of lecturer sees as in the figure 3.3, if we replace the current system with a biometric system it will be successful. Overall these statistics, the lecturer is not satisfied about the existing attendance system.
3.3 Requirements Elicitation
The requirements are the descriptions of the system services and constraints.
3.3.1 Functional Requirements
System functional requirement describes activities and services that must provide.
- Taking and tracking student attendance by facial recognition in specific time.
- Sending the names of the absent student directly to the lecturer
- Permitting the lecturer to modify the student absent or late.
- Showing the names of who is absent or late in the screen to avoid errors.
3.3.2 Non-Functional Requirements
Nonfunctional Requirements are characteristics or attributes of the system that can judge its operation. The following points clarify them:
- Accuracy and Precision: the system should perform its process in accuracy and Precision to avoid problems.
- Modifiability: the system should be easy to modify, any wrong should be correct.
- Security: the system should be secure and saving student’s privacy.
- Usability: the system should be easy to deal with and simple to understand.
- Maintainability: the maintenance group should be able to fix any problem occur suddenly.
- Speed and Responsiveness: Execution of operations should be fast.
3.3.3 User Requirements or Domain requirements
Tools that the user must have in order to use the system and obtain good results:
- Software Requirements: windows7 or higher, SQL and visual studio.
- Hardware Requirements: high resolution camera and screen.
3.4 Requirements Specification
Use case diagram is one of Unified Modeling Language (UML) that describes the system functionality, what actors that interact with the system and any associations between use cases.
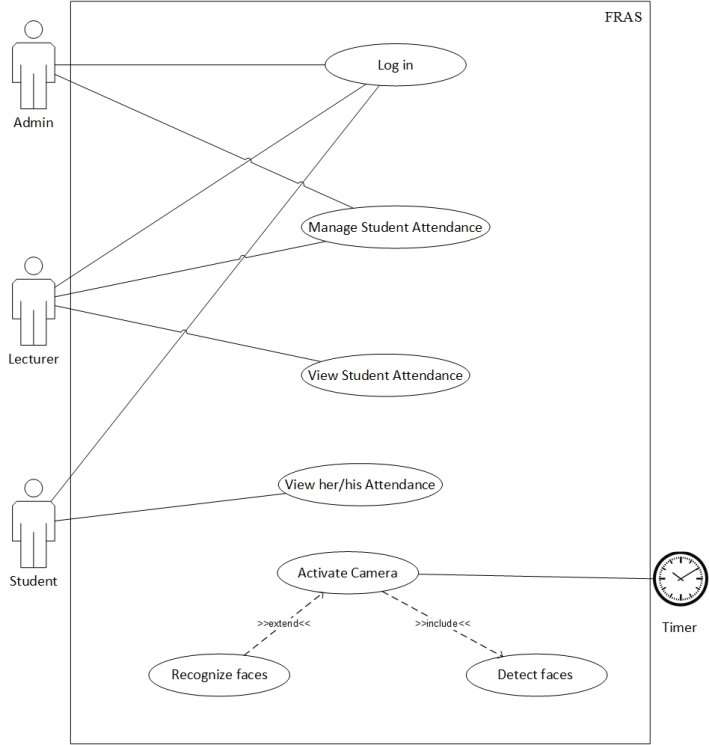
As shown in figure 3.4, the FRAS has actors named Admin, Lecturer and Student which are the main users of the system. Other actor, timer which turns camera on to record attendance by detecting and recognizing faces.
3.4.1 Use Case Description (Detailed Use Cases)
(1) Log in
Table 3.1: Log-in usecase description
|
Use Case Name: |
Log in |
Use Case Number:1 |
|
Actors: |
Admin, Lecturer, student |
|
|
Description: |
This use case describes how Admin, Lecturer and student log into the system. |
|
|
Triggering events: |
Lecturer, admin and student enter his username and password. |
|
|
Steps Performed (Main Path): |
1-System requires users to enter username/password. 2-Users enter username/password. 3-System validate entered username/password. 4-The use case ends successfully. |
|
|
Preconditions: |
|
|
|
Post-conditions: |
Log in is successfully. |
|
|
Alternate: |
If the Admin, Lecturer and student is not fill correctly, the log in fails. |
|
(2) Manage student attendance.
Table 3.2: Manage student attendance usecase description
|
Use Case Name: |
Manage student attendance |
Use Case Number: 2 |
|
Actors: |
Admin, Lecturer. |
|
|
Description: |
Admin and lecturer can modify student attendance (delete, record and alter). |
|
|
Triggering events: |
Information about attendance and absent will be update. |
|
|
Steps Performed (Main Path): |
|
|
|
Preconditions: |
Admin, Lecturer must logged-in their page. |
|
|
Post-conditions: |
New information will be stored in the database. |
|
|
Alternate: |
||
(3) View student attendance.
Table 3.3: View student attendance usecase description
|
Use Case Name: |
View student attendance. |
Use Case Number: 3 |
|
Actors: |
Lecturer. |
|
|
Description: |
Display student attendance. |
|
|
Triggering events: |
Lecturer checking students’ attendance. |
|
|
Steps Performed (Main Path): |
|
|
|
Preconditions: |
Lecturer must logged-in their page. |
|
|
Post-conditions: |
Attendance displayed. |
|
|
Alternate: |
||
(4) View his/her information.
Table 3.4: View his/her attendance usecase description
|
Use Case Name: |
View his/her attendance |
Use Case Number:4 |
|
Actors: |
Student. |
|
|
Description: |
Display student information and attendance. |
|
|
Triggering events: |
Student checking the attendance. |
|
|
Steps Performed (Main Path): |
|
|
|
Preconditions: |
Student must log- in his page. |
|
|
Post-conditions: |
Information displayed. |
|
|
Alternate: |
||
(5) Activate camera.
Table 3.5: Activate camera usecase description
|
Use Case Name: |
Activate camera. |
Use Case Number: 5 |
|
Actors: |
Timer. |
|
|
Description: |
When the class start, the timer will open the camera |
|
|
Triggering events: |
The camera will recognize and detect students’ faces. |
|
|
Steps Performed (Main Path): |
|
|
|
Preconditions: |
Set up lecture information. |
|
|
Post-conditions: |
Captured image sent to FRAS. |
|
|
Alternate: |
||
3.5 Developmental Methodology
In following part, we describe how our system will work step by step along with the system requirement (equipment, software and tools), the methods of collecting data and our project constraints.
First, the workflow of our system is:
- Camera detects and recognize students’ faces
- Sent the captured pictures to the system that compare the sent pictures with retrieved images from the database which contains students’ information and images.
- Mark attendance for the person whose captured image match retrieved image.
- Finally, the result will be shown at the display board attached with the camera.
Second, the system needs are:
The equipment we need are high definition camera to detect and recognize faces and electronic display board to show the result. For tools, we may need a strong and secure communication channel to send image and receive result. In addition, MS Visual Studio (VS) to develop our windows application and MS SQL Server Management Studio to build database are needed software.
Finally, data collection methods and constraints:
We collect data through many ways, one of them is online survey which is Quantitative data collection method. The other is the observations which is Qualitative data collection method. The constraint imposed on our project that it may cannot be applied in the girls’ section.
3.6 Summary
Within this chapter, statements of analysis existing systems and system requirements were presented with functional, nonfunctional and user requirements. The analysis of these requirements was displayed in a model of UML diagrams; use case diagram. We provide a description for each use case to show more details about the system. Software programs, workflow and equipment needed to complete this work were presented with a brief description.
4.1 Introduction
This chapter provides an idea of FRAS design. Simple architecture of the new system, class diagram and sequence diagram will be presented.
4.2 Architectural design
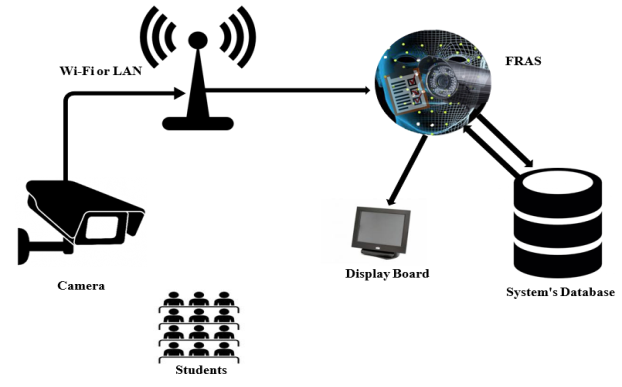 In figure 4.1 we show the system architecture in which the camera detects and recognize students’ faces then sent the captured pictures to the system that compare the sent pictures with retrieved images from the database which contains students’ information and images. Once the recognized face match a retrieved image, the attendance is marked for that person and the attendance sheet is updated. If there are missed faces while detecting and recognizing the process, the process will work repeatedly until all faces recognized. Finally, the result will be shown at the display board attached with the camera.
In figure 4.1 we show the system architecture in which the camera detects and recognize students’ faces then sent the captured pictures to the system that compare the sent pictures with retrieved images from the database which contains students’ information and images. Once the recognized face match a retrieved image, the attendance is marked for that person and the attendance sheet is updated. If there are missed faces while detecting and recognizing the process, the process will work repeatedly until all faces recognized. Finally, the result will be shown at the display board attached with the camera.
4.3 Object Oriented Design Figure
4.3.1 Structural Static Models
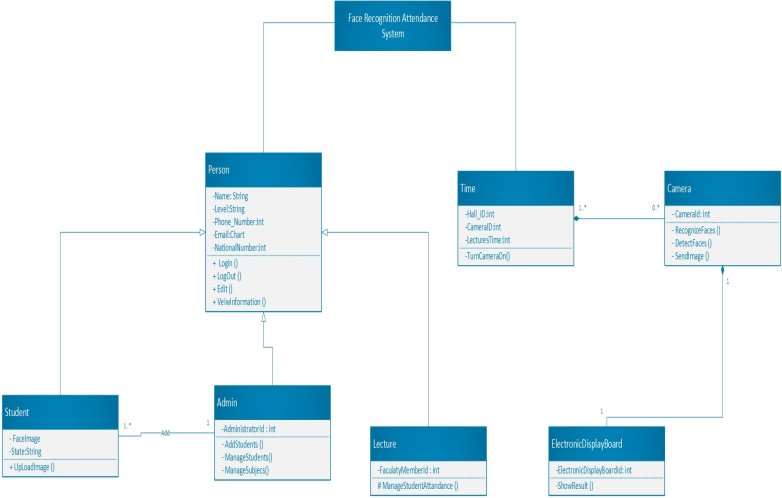 Class diagrams are the extremely utilized UML diagram. It is the key building block of any OO application. It displays the classes, attributes, and methods of each class and the relationship between the classes. [11]
Class diagrams are the extremely utilized UML diagram. It is the key building block of any OO application. It displays the classes, attributes, and methods of each class and the relationship between the classes. [11]
As can be seen from the Figure 4.2, there are three classes sharing common attributes and are inherited from Person class that holds the shared attributes, they represent the actors of the system.
And there is a Time class which has composition relationship with Camera class meaning that if there not setup time to turn the camera on it will not w
 Fast Face detection
Fast Face detection