FPGA Stage for Application-Level Network Security
A Self-Versatile FPGA Stage for Application-Level Network Security
A Research Report for the DSCI 60998 Capstone Project in Digital Sciences Course Vamsi Krishna Chanupati
Ramya Ganguri Kent State University Fall Semester, 2016
Abstract
Wireless communication networks are subjected to vulnerable attacks. The extent of attacks is rising day by day. The proposed work shows the extent of attacks growing in every-day life and a counter method to minimize the extent of these vulnerable attacks. Several studies shows that new and more stable security methods need to be developed by considering information safety, confidentiality, authentication and non-repudiation in the wireless sensor networks. The proposed study shows a self-adoptable FPGA Stage for Application-Level Network Security using application-independent core process IP, UDP and TCP protocols as well as ARP and ICMP message plots. The altered quickened figure outline utilizes information subordinate changes, and can be utilized for quick equipment, firmware, programming and WSN encryption frameworks. The approach exhibited demonstrated that figures utilizing this approach are more averse to endure interruption of differential cryptanalysis than as of now utilized famous WSN figures like DES, Camellia. In this report an overview of existing FPGA algorithms for application level network security is examined and a new FPGA algorithm is proposed.
Keywords: FPGA, WSN encryption, computer aided systems design.
Introduction
The Purpose of the Study (Statement of the Problem)
With the developing dependence of business, government, and additionally private clients on the Web, the interest for fast information exchange has swelled. On a specialized level, this has been accomplished by enhanced transmission advancements: 10 Gb/s Ethernet is now in across the board reasonable use at the ISP and server farm levels, gauges for 40 Gb/s and 100
Gb/s speeds have as of now been figured. The information volume exchanged at these velocities introduces a huge test to current efforts to establish safety, particularly while going past straightforward firewalls and additionally considering payload assessment, or even application- level conventions.
Wireless Sensor Networks are most pre-dominant with this speeds and it is very difficult for customary programmable processors are to stay aware of these speeds. A wireless sensor network (WSN) is a gathering of spatially dispersed, free gadgets that gather information by measuring the physical or ecological conditions. A portion of the conditions are being measured is temperature, weight, dampness, sound, position, lighting, and use data. These readings, as information, are gone through the network, are ordered and sorted out, and later it is conveyed to end client. WSNs are utilized for some applications like power framework controls, modern process checking and control, human wellbeing observing.
Generally, these WSNs tend to require a considerable measure of energy to work, yet diminishing the power is needed for the framework, It builds the lifespan of the sensor gadgets and also leaving space for the battery-fueled applications. As an option, both programming customized committed system handling units and equipment quickening agents for these operations have been proposed. The utilization of reconfigurable rationale for the last permits more noteworthy adaptability than hardwiring the usefulness, while yet permitting full-speed operation. This research gives a detailed description of present day FPGA (Field Programmable Gate Array) and examines the extent of security level standards in the existing FPGA algorithms.
The proposed research study has free key preprocessing which gives elite in regular keys trade. The prime objective of this research is to design an application level network security algorithm using FPGA. This research incorporates the study of various possible threats and vulnerable attacks in wireless communications networks and their effects. It includes the detailed study of design and implementation of application level network security algorithms on FPGA (Field Programmable Gate Array)
The Justification/Significance of the Study
This research proposes a self-adoptable FPGA Stage for Application-Level Network Security for application level wireless network security. A lot of research is required on wireless network security, to improve the performance efficiency and to make the system smart. The research on the latest trending technologies, and a proposed solution to a problem will be carried out in this project, hence it is justified.
This research study is a part of huge project, which involves the use of FPGA for network security. The basic design of the proposed research remains the same although the scale of the projects varies. The study will include the research in FPGA algorithm development WSN encryption and computer aided systems design. Different views on the technology design, its applications and implementation will be presented in the research report.
This research also adds to current research going on in field of the application level wireless network security, Data encryption and crypto-analysis.
The Research Objectives
The objectives of this research are Wireless level networks and analysis of security issues
- This step involves the study of the existing techniques in wireless network security. The research of the existing literature reveals that the wireless sensor network security techniques have been proposed for network security by some researchers and the existing models does not consider the use of feistel ciphers in the research. Design of the algorithm model – The model to be proposed uses self-adoptable FPGA (Field Programmable Gate Array) for application level network security.
A new FPGA based algorithm is designed in order to decrease the extent of attacks in application level network security. It shows that new and more stable security algorithms need to be developed to provide information safety and confidentiality in the networks. This is useful in minimizing the vulnerable attacks in application level networks. There are several other indirect applications of the model to be proposed.
Literature Review
A survey on FPGA for network security that was presented by Muhlbach (2010) depicts an execution of an intrusion detection system (IDS) on a FPGA for network security. Various studies have analyzed string-coordinating circuits for IDS. A strategy for producing a string based coordinating circuit that has expandability of handling information width and radically lessened asset prerequisites. This circuit is used for packet filtering for an intrusion protection system (IPS). An apparatus for consequently creating the Verilog HDL source code of the IDS circuit from rules set is developed, utilizing the FPGA and the IDS circuit generator, this framework can redesign the coordinating origin relating to new interruptions and attacks. The IDS circuit on a FPGA board has been assessed and its exactness and throughput is calculated.
There are various methods, which depicts the usage of Simple Network Intrusion Detection System (SNIDS) detailed explanation is given by Flynn, A (2009), basic equipment arrange interruption recognition framework focusing on FPGA gadgets. SNIDS snoops the activity on the transport interfacing the processor to the Ethernet fringe center and identifies the Ethernet outlines that match a predefined set of examples demonstrating malevolent or refused content. SNIDS depends on an as of late proposed engineering for high-throughput string coordinating. This method executes the SNIDS utilizing the Xilinx CAD (Computer Aided Design) devices and tests its operation on a FPGA gadget. Moreover, programming instruments that empower programmed era of a SNIDS center coordinating a predefined set of examples.
They exhibit the utilization of SNIDS inside a practical FPGA framework on a chip associated with a little system.
Chan et al. exhibited that the PIKE plans include lower memory stockpiling necessities than arbitrary key circulation while requiring practically identical correspondence overheads.
PIKE is as of now the main symmetric-key predistribution plot which scales sub-straightly in both correspondences overhead per hub and memory overhead per hub while being flexible to an enemy fit for undetected hub bargain. PIKE appreciates a uniform correspondence design for key foundation, which is difficult to irritate for an assailant. The dispersed way of PIKE likewise does not give a solitary purpose of inability to assault, giving versatility against focused assaults.
There are certain challenges to be overcome while designing an FPGA algorithm for application level network security, a detailed explanation and analyses is given in (Koch Cho., 2007). The first and difficult challenge is designing an FPGA based algorithm for network security. The system to handle and analyze such data should be super-fast and compatible. The existing hardware is able to do many operations to handle the data; however, special computing systems should be designed to process larger data in shorter time. Another challenge in this area is to secure the data that is generated by multiple sources of different nature. The data needs to be processed before analyzing it for pattern discovery. The data generated is not necessarily complete because of different usage cases of the device. In addition, this feature is used to predict the events of a device and manage every other device and network connected to the device for efficiency, performance and reliability.
Preparing abilities in wireless network hubs are ordinarily in view of Digital Signal Processors (DSPs) or programmable microcontrollers. In any case, the utilization of Field Programmable Gate Arrays (FPGAs) gives particular equipment innovation, which can likewise be reprogrammable in this way giving a reconfigurable wireless network framework. The incomplete reconfiguration is the way toward altering just areas of the rationale that is executed in a FPGA. Accordingly, the comparing circuit can be adjusted to adjust its usefulness to perform diverse assignments. This adjustment ability permits the usage of complex applications by utilizing the fractional re-configurability with low power utilization. This last element additionally speaks to a critical perspective when FPGAs are connected in wireless network frameworks. These days, the wireless network frameworks are required to give an expanding exactness, determination, and accuracy while diminishing the size and utilization. Also, FPGAs and their fractional re-configurability permit us to furnish wireless network frameworks with extra properties like high security, preparing abilities, interfaces, testing, arrangement, and so on.
The present capacities of FPGA designs permit not just execution of basic combinational and consecutive circuits, additionally the incorporation of abnormal state delicate processors.
The utilization of incorporated processors holds numerous uncommon points of interest for the fashioner, including customization, out of date quality moderation, and segment and cost lessening and equipment increasing speed. FPGA implanted processors utilize FPGA rationale components to fabricate inside memory units, information and control transports, interior and outer fringe and memory controllers. Both Xilinx and Altera give FPGA gadgets that install physical center processors worked inside the FPGA chip. These sorts of processors are called “hard” processors. Such is the situation for the PowerPCâ„¢ 405 inside Virtex-4 FPGA gadgets from Xilinx and the ARM922Tâ„¢ inside Excalibur FPGA gadgets from Altera. Delicate processors are microchips whose design is completely constructed utilizing a hardware description language (HDL). The proposed research uses an efficient method of Self-adoptable FPGA Stage for Application-Level Network Security.
Research Design
Description of the Research Design
Wireless communication is one of the latest and the revolutionary technology of the last decade. It intends to connect every device on the planet wirelessly. This number could be billions or even trillions. These communication networks have higher transmission speeds and capable of handling the entire load. Security of this wireless communication network plays an important role to keep it robust and yet flexible.
Network security is a basic issue for the application of new technologies in every aspect of society and the economy. It is especially critical for e-exchanges, where it is an essential to provide security for the transactions. The future threats to network security are still severe. As per a Computer Security Institute (CSI) survey, companies reported average annual losses of the $168,000 in 2006 and $350,424 in 2007, up forcefully from (Hao Chen &Yu Chen, 2010).
This data reflects both the serious circumstance of system security, and also individual’s accomplishment in this issue. Focused on attacks have turned into a pattern in system security. A focused attack is a malware targeted to a particular segment. Around 20% of the respondents of the CSI review endured this sort of security attacks are turning out to be more prominent than any time in recent time.
Among the type of notorious target attacks, Denial-of-Service (DoS) attack is the most threatening system security. Since 2000, DoS attacks have become quickly and have been one of the significant dangers to the accessibility and unwavering quality of system based administrations. Securing the network infrastructure has turned into a high need because of its fundamental impacts for data protection, ecommerce and even national security (Hao Chen &Yu Chen, 2010). Data security principally concentrates on information, data protection and encryption. The following are some of the Requirements for a Successful Security Application.
- Real-Time Protection: It is key for a powerful data instrument to process information at line-speed with moderate cost. All the data movement is subjected for examination in a convenient way, and alerts are produced precisely when unusual circumstances happen.
- Flexible Updating: Constantly developing malicious attacks require security answers for be versatile to hold viability. The redesign could be of the learning databases (marks) that the security examination relies on upon, another answer for determining, or even the framework itself. Redesigning an application will frequently be more functional than supplanting it practically speaking.
- Well Controlled Scalability. Scalability is another basic concern toward functional development. Numerous reported approaches function admirably on a little scale look into system, be that as it may, their execution weakens quickly when conveyed to down to earth scale systems, for example, grounds level systems on the other hand bigger. The principle purpose behind this is framework multifaceted nature for the most part increments at a much more noteworthy rate than the system.
In contrast to programming executions, application oriented and very parallel plan standards make equipment usage prevalent as far as execution. For instance, Transmission Control Protocol (TCP) Stream Reassembly and State Tracking, an Application Specific Integrated Circuit (ASIC) could dissect a solitary TCP stream at 3.2Gbps in (M. Necker, D. Contis 2002). A FPGA-based TCP-processor created by Open Network Laboratory (ONL) was equipped for checking 8 million bidirectional TCP streams at OC-48 (2.5Gbps) information rate. ASIC-based gadgets not just have the upside of elite, accomplished through circuit plan committed to the errand, yet have the potential for low unit cost. Notwithstanding, generous cost alleviation from enormous non-repeating building venture must be accomplished when ASIC gadgets accomplish adequately high-volume creation. Shockingly, this may not be appropriate to network security applications. Steady developing guidelines and prerequisites make it unfeasible to manufacture ASIC-based system security applications at such a high volume. In addition, custom ASICs offer practically zero reconfigurability, which could be another reason that ASICs have not been generally connected in the system security zone.
Reconfigurability is a key prerequisite for the accomplishment of equipment based system security applications and the accessibility of reconfigurable equipment has empowered the plan of equipment based security applications. A reconfigurable gadget could be considered as a hybrid equipment/programming stage since reconfigurability is utilized to stay up with the latest. FPGAs are the most illustrative reconfigurable equipment gadgets. A Field-Programmable Gate Array (FPGA) is a kind of broadly useful, multi-level programmable rationale gadget that can be customized. At the physical level, rationale squares and programmable interconnections make the principle structure out of a FPGA. A rationale square more often than not contains a 4- input look-into table (LUT) and a flip slump for essential rationale operations, while programmable interconnections between pieces permit clients to actualize multi-level rationale. At the plan level, a rationale circuit chart or a high level hardware description language (HDL), for example, VHDL or Verilog, is utilized for the programming that indicates how the chip ought to work. In the gadgets business it is imperative to achieve the market with new items in the briefest conceivable time and to lessen the monetary danger of executing new thoughts. FPGAs were immediately embraced for the prototyping of new rationale outlines not long after they were designed in the mid 1980s because of their one of a kind component of adaptability in equipment improvement. While the execution and size of FPGAs restricted their application in, thickness and speed have brought about narrowing the execution hole amongst FPGAs and ASICs empowering FPGAs to serve as quick prototyping devices as well as to wind up essential parts in installed networks.
Description of the Subject Matter(and/or), Procedures, Tasks
Current FPGAs share the execution favorable position of ASICs in light of the fact that they can execute parallel rationale works in equipment (Flynn, A., 2009). They additionally share a portion of the adaptability of implanted system processors in that they can be powerfully reconfigured. The architecture of reconfigurable network platform, called Net Stage/DPR. The application-free center uses IP, UDP and TCP conventions and additionally ARP and ICMP messages. It has a hierarchical design plan that permits the quick expansion of new conventions in modules at all layers of the systems administration.
From figure 1, Handlers are connected to the core by using two different shared buses with a throughput of 20 Gb/s each, one for the transmit and one for the receive side. Buffers boost the different processing stages and limit the impact of Handler in the processing flow. The interface between the buffers and the actual handlers acts as a boundary for using dynamic partial reconfiguration to swap the handlers to and fro as required.
All handlers have the same coherent and physical interfaces to the center framework. The physical interface comprises of the association with the buffers, strategic flags, for example, clock and reset. However, the handlers communicate with the rest of the framework simply by sending and accepting messages (not really relating to real system bundles). These messages comprise of an inner control header (containing, e.g., charges or state information) and (alternatively) the payload of a system bundle. In this form, the physical interface can stay indistinguishable over all handlers, which significantly rearranges DPR. For a similar reason, handlers ought to likewise be stateless and utilize the Global State Memory benefit by the Net Stage center rather (state information will then simply turn out to be a piece of the messages).
This approach avoids the need to explicitly reestablish state when handlers are reconfigured.
Incoming packets must be routed to the fitting Handler. In any case, utilizing the Handler may really be arranged onto diverse parts of the FPGA. In this manner, we require an element routing table that coordinates the message encapsulated payloads to the suitable administration module. Our routing table has the standard structure of coordinating convention, attachment, and address/net mask information of an approaching bundle to discover the related Handler and it can get information for a whole subnet. On the transmitting side, handlers store active messages into their departure cushions, where they will be grabbed by the center for sending. This is done utilizing a straightforward round-robin approach, yet more perplexing plans could, obviously, be included as required. On the off chance that bundles are bound for a Handler with a full entrance cradle, they will be disposed of. Nonetheless, since the greater part of our present handlers can work at any rate at the line rate; this will not happen with amid standard operation. Bundles for which a Handler is accessible disconnected (not yet arranged onto the gadget) will be checked before being disposed of, in the long run bringing about arranging the Handler onto the FPGA.
This technique does not ensure the gathering of all bundles yet speaks to a decent tradeoff between speed what’s more, many-sided quality. In this case that no fitting Handler exists bundles will be discharged immediately.
From Figure 2, The system can perform the self-ruling of a host PC. A committed equipment unit is utilized as Controller of an implanted delicate center processor, since the last would not have the capacity to accomplish the high reconfiguration speeds. Since of the capacity prerequisites the Handler bit streams are put away in an outside SDRAM memory, and sustained into the on-chip arrangement get to port (ICAP) by utilizing quick exchanges. For effective results, underlying execution requires isolate bit streams for each Handler, comparing to the physical area of the in part reconfigurable regions. To this end, the SDRAM is composed in groups, which hold various forms of every Handler, tended to by the Handler ID and the objective Slot number. For more accurate implementation we set the group estimate to the normal size of every Handler’s bit stream. In a more refined execution, we could utilize a solitary bit stream for every Handler, which would then be moved to the objective Slot at run-time, and bit stream pressure strategies to encourage lessen its size.
A rule based adjustment system is executed in the Adaptation Engine that deciphers packets measurements. In particular, bundles at the attachment level got in a period interval.
These measurements are kept for packets for which a Handler is really accessible. The design looks for quick run queries and insights upgrades (few cycles) not withstanding for high packet rates (10 Gb/s, bundle estimate < 100 B).
Since they depend on similar information structures, the Packet Forwarder and the Adaptation Motor are acknowledged in a typical equipment module. It contains the rationale for following insights, deciphering rules, and overseeing Handler-Slot assignments. Double ports Block RAMs are utilized to understand the 1024-section Rule and 512-section Counter Tables.
Hence, queries to decide the Slot of the goal Handler for an approaching bundle can be performed in parallel to the run administration what’s more, counter procedures. For range proficiency, the CAM is shared between the capacities. Be that as it may, since the throughput of the framework is straightforwardly influenced by the Packet Forwarding execution, the comparing opening steering queries will dependably have need while getting to the CAM. Since the CAM is utilized quickly for every procedure, it won’t turn into a bottleneck. The Packet Forwarder rationale puts the goal Handler opening for an approaching parcel in the yield line. The sending gaze upward is pipelined: by beginning the procedure when convention, IP address and port number have been gotten, the looked-into goal opening will by and large be accessible when it is really required (once the bundle has gone through the entire center convention handling). Since parcels will be neither reordered nor dropped some time recently the Handler arrange, basic lines suffice for buffering look-into results here. Since not every approaching parcel ought to be numbered (e.g., TCP ACKs ought to be disregarded), the Adaptation Engine utilizes a different port to upgrade the Counter Table just for particular bundles. The Rule Management subsystem acknowledges orders from the administration organize interface through a different FIFO, and has an inward FIFO that monitors accessible line addresses in the Rule Table.
From Figure 3, The FPGA locales for every Slot have been measured to 1920 LUTs (only twice as the normal module measure). All openings have rise to region about demonstrate that module sizes are moderately close. This rearranges the adjustment handle, since else we would need to play out different sweeps while selecting on-line/disconnected hopefuls (one for each unique Slot measure class). The dynamic halfway reconfiguration times and the subsequent number of conceivable reconfigurations every second for the ICAP recurrence of 100 MHz we utilize. We demonstrate the times not just for the 1920 LUT Slots we have utilized additionally for both littler and bigger decisions (the best size is application-subordinate). By and large, LUTs are not rare while acknowledging bigger Slots; however the predetermined number of accessible Block RAMs can oblige a plan to fewer than 16 Slots if a Slot requires committed Block RAMs. Considering the total adjustment operation, the time required is ruled by the real reconfiguration time, as ICAP throughput is the restricting figure. Every single different process is fundamentally speedier. For instance, the procedure to look over every one of the 512 Counter Table passages to locate the following competitors requires just around 3µs at 156.25MHz clock speed, an immaterial time relative to the reconfiguration time (Hori Y, Satoh.2008)
Possible Errors and Their Solutions
The following are the possible errors accustomed in FPGA, tampering threats such as destructive analysis, over- and under-voltage analysis, and timing analysis. Using destructive analysis, each layer of the device is captured to determine its functionality. This process requires expensive equipment and expertise. Timing analysis and over- and under-voltage analysis do not require expensive equipment, but are error prone, so are less frequently used to reverse-engineer complex FPGA designs. Also, timing analysis on an FPGA is deterministic, so the time taken from input to output can be determined by passing a signal through a multiplexer.
Findings
Wireless communication is one of the latest and the revolutionary technology of the last decade. It intends to connect every device on the planet wirelessly. This number could be billions or even trillions. A Self Adoptable FPGA for application level network security is must in order to have effective network security (Sascha & Andreas, 2014). Since they depend on similar information structures, it contains the rationale for following insights, deciphering rules, and overseeing Handler-Slot assignments. Block RAMs are utilized to understand the section Rule and section Counter Tables. This method has very low security and the security standards can be easily cracked.
(Deng et al. R. Han, 2006) created INSENS, a protected and Intrusion tolerant routing algorithm for application level security in wireless Sensor Networks. Excess multipath routing enhances interruption resilience by bypassing malignant nodes. INSENS works effectively in the nearness of interlopers. To address asset requirements, calculation on the network nodes is offloaded to asset rich base stations, e.g. registering routing tables, while low-multifaceted nature security techniques are connected, e.g. symmetric key cryptography and one-way hash capacities. The extent of harm delivered by interlopers is further constrained by limiting flooding to the base station and by having the base station arrange its bundles utilizing one-way grouping numbers.
(Kang et al. K. Liu 2006) investigated the issue of versatile network routing algorithm. Regardless of the possibility that area data is checked, nodes may in any case get into mischief, for instance, by sending an extreme number of packets or dropping packets. To powerfully maintain a strategic distance from un-trusted ways and keep on routing packets even within the sight of attacks, the proposed arrangement utilizes rate control, parcel planning, and probabilistic multipath routing joined with the trust-based course choice. They examined the proposed approach in detail, sketching out effective decisions by considering conceivable attacks. They analyzed the execution of their strong network routing protocol and its performance in various situations.
Several algorithms are proposed by researchers in order to improve the efficiency of application level network security, every method has its own merits and demerits. A new method to improve the algorithmic efficiency has been proposed in this research by examining all the previous algorithms. Proposed method will be high efficient when it is related to the existing techniques. The new algorithm proposed uses spacecraft network standards of communications by upgrading the data transfer processing speed to higher performance speeds with the available standards.
Analysis
This research is concept based and discusses the feasibility of FPGA in application level wireless communication networks to enhance applications. This study reviews the existing literature thoroughly and also proposes the use of FPGA to be applied as the next version to the application level network security
The model to be proposed uses self-adoptable FPGA for application level network security. A new FPGA based algorithm is designed in order to decrease the extent of attacks in application level network security. It shows that new and more stable security algorithms need to be developed to provide information safety and confidentiality in the networks. This is useful in minimizing the vulnerable attacks in application level networks.
The applications of the proposed model are infinite. FPGA intends to strong network security. Therefore, these are not specific to any field or application. There are different classifications of the applications. These classifications are required for better understanding and not necessarily research requirements. These are useful to the users in a way that increases the extent of safety and security of data in wireless data transmission. The performance analysis in network security is determined based of the extent of vulnerable attacks. The proposed algorithm is not tested further research is required for implementing this algorithm in a real time platform.
Conclusions
Restatement of the Problem
With the developing dependence of business, government, and additionally private clients on the Web, the interest for fast information exchange has swelled. On a specialized level, this has been accomplished by enhanced transmission advancements: 10 Gb/s Ethernet is now in across the board reasonable use at the ISP and server farm levels, gauges for 40 Gb/s and 100 Gb/s speeds have as of now been figured. The information volume exchanged at these velocities introduces a huge test to current efforts to establish safety, particularly while going past straightforward firewalls and additionally considering payload assessment, or even application- level conventions.
Customary programming programmable processors are painfully squeezed to stay aware of these speeds. Wireless Sensor Networks are most pre-dominant with this speeds and it is very difficult for customary programmable processors are to stay aware of these speeds. A wireless sensor network (WSN) is a gathering of spatially dispersed, free gadgets that gather information by measuring physical or ecological conditions. Utilization of reconfigurable rationale for the last permits more noteworthy adaptability than hardwiring the usefulness, while as yet permitting full-speed operation. This research gives a detailed description of present day FPGA
(Field Programmable Gate Array) and examines the extent of security level standards in the existing FPGA algorithms.
This research incorporates the study of various possible threats and vulnerable attacks in wireless communications networks and their effects. It includes the detailed study of design and implementation of application level network security algorithms on FPGA.
New Knowledge Discovered
The proposed research thoroughly analyzes the implementation of FPGA for application level network security. The existing methods and approaches are used in the system and the flow of data is understood. Then the loop of the system is completed with the proposed research that discusses about the usage of FPGA for application level network security, and therefore making it smart With the implementation of such a system it will not only be able to take sense the input but will also be able to predict the user habit and act accordingly.
Net Stage FPGA has exhibited that it is not just achievable to perform application-level (rather than simply the parcel level) arrange handling in FPGAs, be that as it may, likewise effectively abuse the dynamic incomplete reconfiguration capacities of current gadgets to construct self-adjusting designs. The base engineering of discrete handling stages that permits the adaptable coordination of new usefulness in light of an equipment based system convention stack is suited to a wide number of areas. Analysis for every stage of the various stages in the implementation of solution that is proposed, is provided.
The proposed algorithm is not tested further research is required for implementing this algorithm in a real-time platform. This research that is covered is one more contribution to an always growing research in the network security. The research on FPGA or network security is not available. Therefore, this research also stands as one among very few research papers on the latest research topic.
This research includes the study on several subjects such as wireless communication networks, Data Mining, Communication protocols, Computer aided systems design, Cognitive Analytics, etc., Therefore it is difficult to associate these topics in to specific subjects from the coursework. Advanced networking concepts are extensively used in the study and design of the method in this research.
Significance of the Findings
The model proposed uses self-adoptable FPGA for application level network security. A new FPGA based algorithm is designed in order to decrease the extent of attacks in application level network security. It shows that new and more stable security algorithms need to be developed to provide information safety and confidentiality in the networks. This is useful in minimizing the vulnerable attacks in application level networks. There is no guarantee that this is the best solution for minimizing vulnerable attacks. A self-versatile FPGA must come together in reducing the extent of vulnerable attacks in wireless communication networks. The use of self- versatile FPGA is already clearly conveyed in this model(research).
Limitations of the Study
The following are the limitations of the study. This research need not consider the challenges that may be encountered while implementing the proposed model. The performance of the existing system is not understood by the statistical, simulation results of the FPGA. Exact technical model for the proposed concept is not provided. At the stage of implementation, it may require some changes.
Recommendations for Further Investigation
The working model of small prototype FPGA application is future scope. It can also provide solid evidence that the concept design is feasible and practical. Performance analysis of various FPGA security algorithm techniques is also considered for implementation which is also considered Future scope.
References
C. Haowen and A. Perrig, (2005) “PIKE: peer intermediaries for key establishment in sensor networks,” in Proc. 2005 IEEE Conf. Computer Commun., pp. 524-535.
Flynn, A., Gordon-Ross, A., George, A.D (2009). Bitstream relocation with local clock domains for partially reconfigurable FPGAs. In: Proc. of the Conference on Design, Automation and Test in Europe, pp. 300-303
Hori, Y., Satoh, A., Sakane, H., Toda, K (2008). Bitstream Encryption and Authentication Using AES- GCM in Dynamically Reconfigurable Systems. In: Proc. of the 3rd Intl. Workshop on Security, pp. 261-278
Katashita, T., Yamaguchi, Y., Maeda, A., Toda, K (2007). FPGA-Based Intrusion Detection System for 10 Gigabit Ethernet. IEICE – Trans. Inf. Syst. E90-D, 1923-1931
Koch, D., Beckhoff, C., Teich, J (2007). Bitstream Decompression for High Speed FPGA Configuration from Slow Memories. In: Proc. of the Intl. Conference on Field- Programmable Technology
Liu, M., Kuehn, W., Lu, Z., Jantsch, A (2009). Run-time Partial Reconfiguration Speed Investigation and Architectural Design Space Exploration. In: Proc. of the Intl.Conference on Field Programmable Logic and Applications
Muhlbach, S., Brunner, M., Roblee, C., Koch, A (2010). Malcobox: Designing a 10 gb/s malware collection honeypot using reconfigurable technology. In: Proc. of the 20th Intl. Conf. on Field Programmable Logic and Applications, pp. 592-595
Figures

Figure 1: Self-adaptable network platform (Hao Chen &Yu Chen, 2010).

Figure 2: Addressing of Handler bit streams in SDRAM (Hao Chen &Yu Chen, 2010).
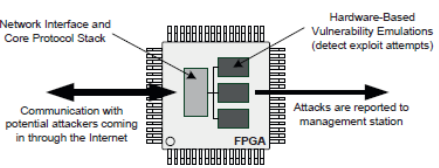
Figure 3: FPGA-based network processing (Hori Y, Satoh.2008)