Network User Problems
a)
Credential, Permission and Rights Problems
The user can have this kind of problem when tries to access/alter a host, folder or document and is not able to because they cannot log in, or they do not have that permission.
Network Performance
If the user or LAN administrator wants to use a wireless connection, it will drastically impact the network communication. This happens because today home-based wireless systems will not produce more than about 54-100 Mbps of transfer. And using a hub instead of a network switch can cause major issues with speed and latency, which means low performance network.
TCP/IP Conflicts
There are many reasons why this can be an issue, but the most common happens when at least two devices are trying to use the same IP address in the same network.
b)
By the morning, an user that works in a company, tries to logon into the Windows operational system using the network credentials given by the Network Administrator. But he gets the following error: “The relationship between this device and the domain failed”. The user tries to restart the computer and logon again, but gets the same error.
c)
 Network Performance
If you are using a corporate network, make sure that you are not streaming or downloading music, video or whatever else while working. By doing that, you will be impacting the network performance and like it will make IP phone calls and file sharing, per example, really slow. The Network Administrator has to find a way to lock down this kind of problems, like blocking music/video streaming and files downloads.
TCP/IP Conflicts
When the Network Administrator faces problems like IP conflicts into the network, the easiest way to fix it would be releasing and renewing the device IP and try to use it again.
d)
|
Knowledge base – form |
||||
|
Name of the company |
TGM Inc |
|||
|
Client’s Name |
Ilson Neves |
|||
|
Date and time |
01/12/2015Â 2:50 PM |
|||
|
Problem Detail: |
||||
|
Users are complaining about devices IP conflicts every day during the usual work. |
||||
|
Signature            Tiago Garcia Mourão |
||||
|
Date |
01 |
12 |
2015 |
|
|
Name of the technician |
Tiago Garcia Mourão |
|||
|
Date and Time |
02/12/2015Â 9:30 AM |
|||
|
Service Hours |
2 hours |
|||
|
Proposed Solution |
||||
|
Release and renew the IP address in every device and then, check the router in order to adjust the number of available IP’s. |
||||
|
Signature            Tiago Garcia Mourão |
||||
|
Date |
02 |
12 |
2015 |
|
|
Resource |
N/A |
|||
|
Costs |
NZD 200,00 |
|||
|
Procedure Personnel |
||||
|
I accessed the CMD in every computer and enter the commands “ipconfig /release” and “ipconfig /renew”. Then, I checked that the internet connection was working properly in every single device. Then, I checked that the amount of devices accessing the network was smaller than the amount of IP’s available. |
||||
|
Signature            Tiago Garcia Mourão |
||||
|
Date |
03 |
12 |
2016 |
|
|
Company contact |
Address |
50, Queen St |
||
|
Information |
Phone |
05 0976394 |
||
|
Website |
www.tgm.co.nz |
|||
1.2 – Fileserver problems:
a)
File Sharing
One of the most common problems related to fileservers is file sharing. When users try to access the folder/document in the server, they can get errors like “Not authorized access” or “The file is being used”.
Data Backup
An important action related to fileservers is the backup. The most of companies have files that need to be accessed many times per day and by different users, no matter what.
b)
A company user created a shared folder on the network to allow other department users read and edit documents. After adding these documents, other users tried to open the documents, but they got the following error: “Windows cannot access the document. You do not have the permission to access the document. Contact your Network Administrator to request access.” The users restarted the PC’s and tried to access the documents again, but still got the same error.
c)
File Sharing
If the users cannot access shared folders or alter shared folders, the Network Administrator has to check the reason. The first step is checking if the folder/file owner has shared it. Otherwise, only him will be able to access it. If it have been done, the next step is checking if the file is being used by another user. After that, the folders/files have to be available for the allowed users in the network.
Data Backup
If the server crashes or the file is deleted by mistake, the Network Administrator has to get the last backup version as soon as possible, no matter what.
d)
|
Knowledge base – form |
||||
|
Name of the company |
MG Enterprise |
|||
|
Client’s Name |
Carlos Silva |
|||
|
Date and time |
01/09/2016Â 4:30 PM |
|||
|
Problem Detail: |
||||
|
Users are complaining that they cannot access or alter any folders or files into the fileserver. |
||||
|
Signature            Tiago Garcia Mourão |
||||
|
Date |
01 |
09 |
2016 |
|
|
Name of the technician |
Tiago Garcia Mourão |
|||
|
Date and Time |
02/09/2016Â 7:30 AM |
|||
|
Service Hours |
3 hours |
|||
|
Proposed Solution |
||||
|
Check the fileserver configuration, the folders/files sharing status and the list of allowed users. |
||||
|
Signature            Tiago Garcia Mourão |
||||
|
Date |
02 |
09 |
2016 |
|
|
Resource |
N/A |
|||
|
Costs |
NZD 300,00 |
|||
|
Procedure Personnel |
||||
|
First, I tried to access the folder and files into the fileserver using the users’ PC. I got the same permission error in every single PC. Then, I went to the data center and checked that the fileserver IP was configured properly. Then, I checked that the folders and files sharing option were OK. And the last step was include all the desired users to the sharing list. After that, I tested all the PC’s and all of them were able to access the folders and files. |
||||
|
Signature            Tiago Garcia Mourão |
||||
|
Date |
03 |
09 |
2016 |
|
|
Company contact |
Address |
5, Welesley St |
||
|
Information |
Phone |
07 9845672 |
||
|
Website |
www.mgenterprise.co.nz |
|||
 1.3 – Performance issues:
a)
Apart of wired connection, the wireless connection can subject your connection to variable conditions. Because of that, the data delays can bring the transfer performance down.
The data transfer over the network does not need much system memory usage, but can affect the performance of other OS components. If the system memory is too low, the system has to access the HD more often, and the writing/reading disk performance will be low as well.
b)
Every week a company leaders need to make a videoconference with another branch for a brainstorm. Both branches use Skype for it, but they are having some problems related to the network. The connection is very slow and the call crashes, even if the computer is connected to the internet using the wire.
c)
Memory (RAM)
In order to increase the network data transfer, the user can add more RAM memory to the laptop/PC, making the writing/reading disk faster and avoiding the HD access.
Wireless
If the user wants to increase the wireless connection performance, the best ways would be getting closer to the Access Point to get a high quality connection or buying a better Access Point, if possible to support more users at the same time.
d)
|
Knowledge base – form |
||||
|
Name of the company |
GT Ltd |
|||
|
Client’s Name |
Bruno Souza |
|||
|
Date and time |
01/02/2017Â 8:50 AM |
|||
|
Problem Detail: |
||||
|
The users are complaining that the wireless connection is too slow and sometimes crashes. |
||||
|
Signature            Tiago Garcia Mourão |
||||
|
Date |
01 |
02 |
2017 |
|
|
Name of the technician |
Tiago Garcia Mourão |
|||
|
Date and Time |
02/02/2017Â 4:30 PM |
|||
|
Service Hours |
5 hours |
|||
|
Proposed Solution |
||||
|
Check the distance between the Access Point and users; and if it supports the amount of users at the same time. |
||||
|
Signature            Tiago Garcia Mourão |
||||
|
Date |
02 |
02 |
2017 |
|
|
Resource |
N/A |
|||
|
Costs |
NZD 500,00 |
|||
|
Procedure Personnel |
||||
|
Using different users laptop’s, I could see that some users had wireless signal was too poor. To those users who got good signal, I checked the internet access speed. It was extremely slow and crashing several times. Checking the amount of users and AP’s, I told the IT manager that the problem was that the company needs more AP’s to spread the signal and to support the amount of users. After installing and configuring some new AP’s, all the users have fast wireless connection. |
||||
|
Signature            Tiago Garcia Mourão |
||||
|
Date |
03 |
02 |
2017 |
|
|
Company contact |
Address |
10, Quay St |
||
|
Information |
Phone |
09 9756729 |
||
|
Website |
www.gt.co.nz |
|||
2.1 – Identify and list any 5 network monitoring tools:
Nagios
One of the best known free tool. The most important part of the tool is the core and it allows you to build plugins to monitor particular elements. It has a large-scale use.
Zenoss
This software was created to monitor server, storage, applications, networks and virtual servers.
Monitis
Focused on small or medium-sized companies, this application can arise as a great network tool.
Pandora FMS
It’s capable of monitoring over 10,000 nodes and monitors servers, networks  and applications. It has many alerts, reports and third party integrations, etc. Its network autodiscovery system can find all the network elements in a short time.
Zabbix
It’s known for being easy to configure and for having a very powerful GUI. It has agentless monitoring service can monitor up to 10,000 nodes without performance issues.
2.2 – Install network monitoring tools:
According to the figure below, during an average websites usage at 3PM, the total traffic size was 4.24MB, the transfer rate was 136.942Kbps and the packets amount was 9,384 (474.000 bytes):
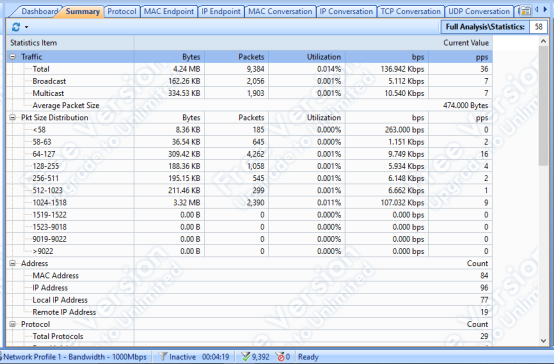
(Figure 01: Capsa Free software – Summary tab)
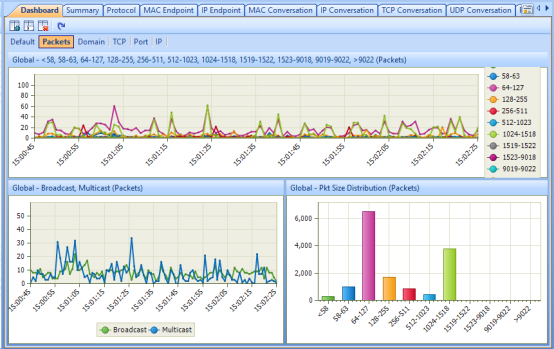
(Figure 02: Capsa Free software – Dashboard tab)
After few minutes, a new Youtube tab was opened at 3:03 PM and then the total traffic size was 35.15MB, the transfer rate was 531.204Kbps and the packets amount was 50,292 (732.000bytes), according to the figure below:
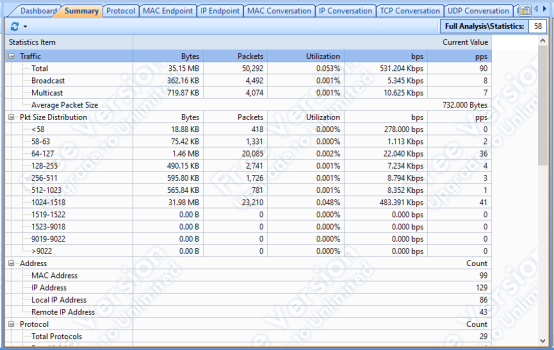
(Figure 03: Capsa Free software – Summary tab)
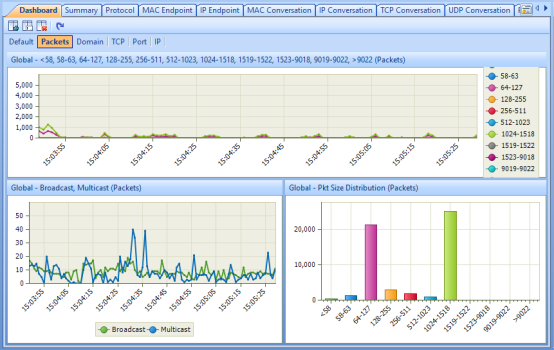
(Figure 04: Capsa Free software – Dashboard tab)
2.3 – Analyse the bandwidth information:
According to the figures above, the usage of network didn’t reach its limits. The maximum usage that it reached during the tests was 0.053% of the bandwidth.
2.4 – Explain different techniques for LAN performance:
Watch everything
Users often complain about the network performance, but the most of times, the network has nothing to do with it. One of the best techniques to improve the LAN performance is monitor everything, from network latency and throughput, to CPU and RAM utilization. Monitoring the switches and routers, the network error rates and configuring some logfiles alerts will make the network faster.
Know your apps
The network is always being consumed by the applications. Even being hard to see exactly what is going on, is possible observing their effects on the infrastructure. The best way to keep your network performance is testing the software in a testing environment before purchasing/installing it in the infrastructure and check the amount of resources is being used.
3.1 – Identify and explain security exposures and violations:
Former Employees
Attacks coming from inside the network are one of the biggest threats to a corporate network. Former employees, especially from IT department, that have the networks, admin accounts and data centers access can spread/sell this information or even hack the company.
Careless Employees
An employee that forgets files or the cellphone/laptop inside a taxi cab or on a restaurant table could allow a malicious person to use this information or sell it to competitor companies.
3.2 – Determine the possible solutions for the CVE:
Former Employees
In order to avoid this kind of danger, when an employee is about to be dismissed, the Information Security Analyst or the Network Administrator has to fill out a form describing all the access rights to be revoked(systems, servers, data centers, etc) and ask to an analyst do it.
Careless Employees
Information stealing is one of the most dangerous ways to get corporate information leaked. To avoid it, employees must look after classified documents, cellphones, laptops, etc and keep it safe. Electronic devices must have passwords, per example.
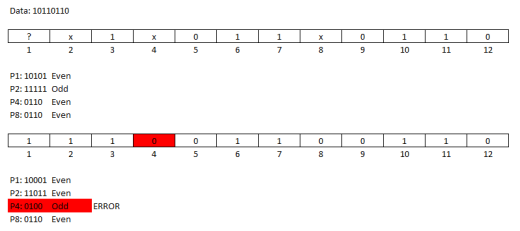
4.1 – The sender in a LAN sends 10110110; a hacker alters the data and the receiver receives 10100110. As a network expert analysis to find out the position of error bit:
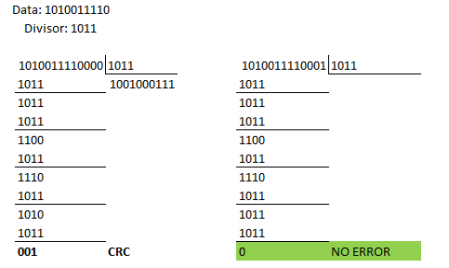
4.2 – Analysis a 10 bit sequence 1010011110 and a divisor of 1011:
Viper Plagiarism Scanner Report
Data Expedition, I. (s.d.). Data Expedition, Inc. Fonte: Data Expedition Inc: http://www.dataexpedition.com/support/notes/tn0009.html
Kosse, T. (s.d.). Tim Kosse. Fonte: https://ftptest.net/: https://ftptest.net/Help
Prigge, M. (1 de June de 2010). IDG Communications, Inc. Fonte: InfoWorld: http://www.infoworld.com/article/2627174/network-monitoring/10-tips-for-boosting-network-performance.html
Schiff, J. L. (20 de January de 2015). IDG Communications, Inc. Fonte: CIO: http://www.cio.com/article/2872517/data-breach/6-biggest-business-security-risks-and-how-you-can-fight-back.html
Shimonski, R. J. (3 de November de 2009). TechGenix Ltd. Fonte: WindowsNetworking.com: http://www.windowsnetworking.com/articles-tutorials/common/Top-5-Networking-Issues-Windows-Clients.html
Steve. (2 de January de 2017). Pandora FMS Team. Fonte: Pandora FMS: https://blog.pandorafms.org/network-monitoring-tools/#comparison