OCTAVE Allegro Risk Assessment Method
Business Application:
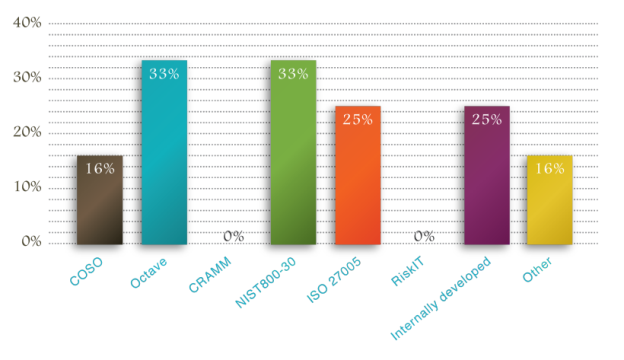
According to a study published by Wisegate, an IT expert knowledge service, in which they as Chief Security Officers about the security methodologies used in their organization, 33% reported OCTAVE Allegro as their framework of choice along with NIST 800 – 30 both sharing top ranks. This highlights the popularity of the OCTAVE Allegro. The key advantage that OCTAVE Allegro provides an organization is the flexibilty to imokement it in parts. As it is comprehensive, organizations select implementation of portions that makses the most business sense to the organization.
The key strength of the OCTAVE Allegro risk assessment method is the all-inclusive consolidation of the threat profiles which provides significant intelligence for threat mitigation for most cases. OCTAVE does not require focus on all assets which is required in some other methodologies and frameworks, thus it saves a lot of time and helps keep the scope relevant ot the business context..
The main focus of OCTAVE Allegro is information assets. OCTAVE Allegro (defined to analyze risks with a greater focus on information assets, as opposed to the approach in information resources). The important assets in an organization are identified and assessed based on the context of how they are used, where they are stored, transported, processed, and how they are exposed to threats, vulnerabilities and disruptions as a result. This process helps reducing the possibility that major data gathering and the analysis are performed for assets that are not well defined. One of the advantages of using OCTAVE Allegro is that it can be performed in a workshop-style, collaborative setting and is supported with all the needed guidance, worksheets, and questionnaires, which are all available online for free. The method is also appropriate for use by individuals who want to perform risk analysis without extensive organizational involvement, expertise, or input.
Information is actually the property as well as other business assets. It is essential for an organization that information is suitably protected. This is especially important in a business environment that is increasingly internetworking with each other and where the information is exposed to a growing number of different types of threats and vulnerabilities. Information can exist in various forms. It can be printed or written on paper, stored or electronically transmitted by regular mail or electronic means, shown on film or in the form of conversation. Information stored in all those formats must always be protected appropriately. According to KPMG, one of the world’s largest auditors, what hasn’t been assessed, can’t be managed [7]. So, the first step in protecting the information is security risk assessment of equipment and procedures used for information processing and storage. This is especially important for institutions where the exploitation of vulnerabilities in information security can lead to significant loss of reputation or direct financial loss. In this paper we present and compare two methods for information security risk assessment. OCTAVE is a more detailed method for assessing information security risks. It is specially recommended for security risk assessment of information containers.
National Institute of Standards and Technology (NIST) recommendations also used for IS risk assessment besides OCTAVE Allegro method. The risk assessment according to NIST is carried out in 9 steps followed by variety of the measures for mitigating risks [2], which is common to the OCTAVE method too. OCTAVE methodology can be further augmented by defining a time frame at the time of selecting measures for information risk reduction. OCTAVE is more precise and provides a more comprehensive outlook at the information risk. Defining the scope of the effort is the first step in assesment of risk according to the NIST guidelines whereas in OCTAVE Allegro method, criteria for measuring risk is dddone first as oer the guidelines of the business entity. The foundation for risk assessment of information assets of an organization is the criteria for measuring risk forms. In the absense of such criteria, measuring the degree to which the business is exposed to an impact if the risk is realized for information assets is not possible. The most important criteria for measuring risk in most organization are Reputation & Customer Confidence, Monetary, Safety, and Legal and Penalties. OCTAVE Allegro methodology is some years newer than NIST guidelines, and since the subtleties of change in current unpredictable business environment, OCTAVE Allegro methodology would therefore be more suitable for security risk assessment. OCTAVE Allegro method also provides tangible and superiorior examples of risk assessment and measures for mitigation risks.
per SANS guidelines, Information gathering is the first phase of risk assessment and it beigins with a step that necessitates creating a lsit of all the assets, including infrastrures, human resources and services used or intented for the system. Recognizing the possible threats is the second step followed by procuring owner’s data sensitivity classification. The fourth step is, identifying organizational and technical vulnerabilities and obtaining owner’s business impact ranking of a loss for all of the following security objectives: Availability, Integrity, Confidentiality, Accountability and Assurance. Those five important business goals are set clear and correctly, but unlike. In OCTAVE Allegro methodology, defining security goals is the second step process whereas, formulating an information asset profile is the third step following the establishment of risk measurement criteria, and that will be vital.
Empirical methods are typically derivative from a formalization of best practices and the theoretical methods which are justified by a formal model are the two main groups into which risk assessment are methods divided. In typically setting, the former is preferred as it approaches provide rational risk evaluations. A good risk assessment methodology should be both hands-on and theoretically complete. OCTAVE Allegro method fits both conditions.
OCTAVE Allegro method provides a thorough and superior quality of analysis and assessment of security risks. OCTAVE methodology enables to measure more accurate and consequently better to reduce the risk of information security for a property. However, OCTAVE Allegro method can be complex and requires much more time and effort when it is applied to the same information security risk assessment of certain assets.
OCTAVE in the Healthcare Industry
OCTAVE risk assessment has been recognized as the preferred methodology for HIPAA compliance, making it relevant to companies that have outsourcing relationships with firms regulated under HIPAA
Department of Health and Human Services (HHS) as per Health Insurance Portability and Accountability Act of 1996 (HIPAA, Title II) is required to establish national standards for the security of electronic healthcare information. It postulates a sequence of administrative, technical, and physical security safety measures for covered entities to use to safeguard the confidentiality, integrity, and availability of personally identifiable electronic health information. The standards are defined into required or addressable implementation specifications.
The standard §164.308(a)(1) is the security management process. It states that a “covered entity must implement policies and procedures to prevent, detect, contain, and correct security violations.” Risk analysis and risk management are required implementation specifications for this standard.
Risk Analysis: Covered entities must conduct an accurate and thorough assessment of the possible risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity.
Risk Management: Covered entities must contrivance security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with the required HIPAA safeguards.
As part of an early initiative to get a head start in meeting Risk Analysis and Risk Management requirements, OCTAVE was endorsed as the chosen information security risk assessment approach by the Security Working Integrated Project Team (WIPT), Office of the Assistant Secretary of Defense/Health Affairs (OASD/HA).
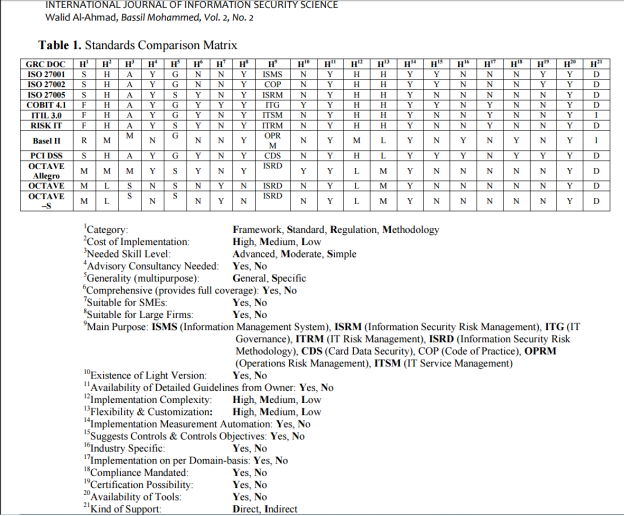
The OCTAVE methods have several important characteristics such as easy to execute and do not require large teams or advanced technical knowledge. They are also flexible and can be customized to address an organization’s particular risk environment, security needs and level of skill. Also, risks are addressed in business contexts providing easy to understand results. It can be used also as the foundation risk-assessment component or process for other risk methodologies in a “hybrid-risk assessment” approach. OCTAVE information security risk assessments covers all information security aspects being physical, technical or people. A drawback in OCTAVE’s various models is that they employ qualitative methodology only as opposed to quantitative approaches. Table 1 presents a detailed comparison matrix between the previously discussed standards.
https://pdfs.semanticscholar.org/f029/7b4707a6f33b041a5e93bb8946ed9b334d99.pdf
http://www.wisegateit.com/resources/downloads/wisegate-risk-based-security-report.pdf