Risk-based Access Control Model for the Internet of Things
Developing an adaptive Risk-based access control model for the Internet of Things
Hany F. Atlam a, c Gary B. Wills a, Robert J. Walters a, Joshua Daniel c
 a Electronic and Computer Science Dept., University of Southampton, UK
b Security Futures Practice, BT Research & Innovation, Ipswich, UK
 c Computer Science and Engineering Dept., Faculty of Electronic Engineering, Menoufia University, Egypt
Abstract-The Internet of Things (IoT) is creating a revolution in the number of connected devices. Cisco reported that there were 25 billion IoT devices in 2015 and modest estimation that this number will almost double by 2020. Society has become dependent on these billions of devices, devices that are connected and communicating with each other all the time with information constantly share between users, services, and internet providers.
The emergent IoT devices as a technology are creating a huge security rift between users and usability, sacrificing usability for security created a number of major issues. First, IoT devices are classified under Bring Your Own Device (BYOD) that blows any organization security boundary and make them a target for espionage or tracking. Second, the size of the data generated from IoT makes big data problems pale in comparison not to mention IoT devices need a real-time response. Third, is incorporating secure access and control for IoT devices ranging from edge nodes devices to application level (business intelligence reporting tools) is a challenge because it has to account for several hardware and application levels. Establishing a secure access control model between different IoT devices and services is a major milestone for the IoT. This is important because data leakage and unauthorized access to data have a high impact on our IoT devices. However, traditional access control models with the static and rigid infrastructure cannot provide the required security for the IoT infrastructure.
Therefore, this paper proposes a risk-based access control model for IoT technology that takes into account real-time data information request for IoT devices and gives dynamic feedback. The proposed model uses IoT environment features to estimate the security risk associated with each access request using user context, resource sensitivity, action severity and risk history as inputs for security risk estimation algorithm that is responsible for access decision. Then the proposed model uses smart contracts to provide adaptive features in which the user behavior is monitored to detect any abnormal actions from authorized users.
Keywords– Security, Internet of Things, Risk, access control, Adaptive, Context.
The Internet of Things (IoT) is growing in different ways. The adoption rate of the IoT is at least five times faster than the adoption of electricity and telephony [1]. Moreover, it is becoming the backbone of the future of the Internet that encompasses various applications and devices. The IoT devices are interconnected using different communication technologies such as wireless, wired and mobile networks [2].
The concept of the IoT was first mentioned by Kevin Ashton in 1999 [3]. He has said, “The Internet of Things has the potential to change the world, just as the Internet did. Maybe even more so”. Later, the IoT was formally presented by the International Telecommunication Union (ITU) in 2005 [4]. The ITU defines the IoT as: “a global infrastructure for the Information Society, enabling advanced services by interconnecting (physical and virtual) things based on, existing and evolving, interoperable information and communication technologies“[5].
The IoT faces many challenges that stand as a barrier to the successful implementation of IoT applications. The security is considered the most difficult challenge that needs to be addressed. This challenge is more complicated due to the dynamic and heterogeneous nature of the IoT system [6], [7]. Authentication and access control models are the essential elements to address the security issue in the IoT. They can prevent unauthorized users from gaining access to system resources, prevent authorized users from accessing resources in an unauthorized manner and allow authorized users to access resources in an authorized manner [8], [9].
The main purpose of the access control is to reject unauthorized users and limit operations of authorized users using a certain device. In addition, it tries to prevent the activity that could cause a security breach [7]. A powerful access control model should satisfy security requirements of confidentiality, integrity, and availability [10]. Traditional access control approaches are static in nature as they depend on predefined policies that always give the same outcome regardless of the situation. They are context insensitive. Furthermore, they require a rigid authentication infrastructure [11], [12]. So they cannot provide for distributed and dynamic environment as the IoT systems [13]. Dynamic access control approaches are more appropriate to the IoT. This is because they are characterized by using not only the policies but also environment features that are estimated in real-time to determine access decisions. The dynamic features can include trust, risk, context, history and operational need [14], [15].
This paper presents an adaptive risk-based access control model for the IoT. This model can dynamically estimate the security risk associated with each access request to make the access decision. It uses real-time user context attributes, resource sensitivity, action severity and risk history as inputs to estimate the security risk value of each access request. In addition, the user behavior is monitored to detect any abnormal misuse.
This paper will start by discussing concepts of access control in the IoT in section II; Section III presents access control challenges in the IoT; Section IV introduces different access control models; Section V discusses the concept of risk-based access control model; Section VI presents the proposed model; Section VII illustrates the process flow of the proposed model; Section VIII presents the related works, and Section IX is the conclusion
The IoT devices send and receive a variety of information about owner’s behavior. Therefore, it is important to protect not only the communication process between IoT devices but also authentication and access control of IoT devices [16]. The access control process works with many layers of the IoT reference model that is shown in figure 1. The control process flows from top to down. Therefore, the access control works with different data whether at storage, at motion, or at IoT device itself. Therefore, the access control is a big issue in the IoT that need addressing.
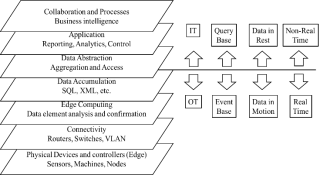
Fig. 1. The IoT reference model [16]
The main function of access control is to grant access rights only to authorized users. Also, it prevents authorized users from accessing system resources in an unauthorized manner [7]. A powerful access control model should fulfill security demands of confidentiality, integrity, and availability [10]. In the IoT, the access control is required to ensure that only authorized users can update device software, access sensor data or command the actuators to perform an operation [17]. There are three ways to implement access control in the IoT systems; centralized, centralized and contextual, and distributed [18].
In the centralized approach, the access control logic is implemented at a central entity. This entity could be a server with direct communication to IoT devices that it manages or another entity in a different location. Therefore, IoT devices send their data to the central entity that is responsible for making access control decisions [18].
In the centralized and contextual approach, IoT devices are not completely passive entities; this is because they participate in the access control decisions. The access control logic is implemented at a central entity as in centralized approach, but the contextual features from IoT devices are sent to the central entity. These features are used to make access decisions [18].
In the distributed approach, all the access control logic is embedded into IoT devices. These devices are being provided with necessary resources to process and send information to other services and devices. Therefore, IoT devices have to have the ability to perform the authorization process without the need for a central entity [18].
Due to the distributed and dynamic nature of the IoT, there are many challenges that should be addressed when implementing an access control model. These requirements include;
- Interoperability with multiple users: Access control policies should be designed to support multiple organizations. For instance, each organization creates its own policies and respect other collaborating organization’s policies [24].
- Dynamic interaction: Access control policies should be predictable and specified in a dynamic and continuous way by considering context changing during the access control process [25].
- Context awareness: The context is considered one of the core features since it enables intelligent interactions between users and IoT devices. Using the context will make access decisions dynamically determined based on surrounding environment features [17].
- Usability: The access control model should be easily administrated, expressed and modified. It also should provide suitable easy to use interfaces for both consumers and devices needs [26].
-  Limited resources: The resources associated with IoT devices such as energy, memory, and processing power are limited due to devices lightweight. Therefore, the access control model designed for the loT should support efficient solutions [17].
- Scalability: The IoT connects billions of devices. The access control model should be extensible in size, structure, and number of devices [17].
- Delegation of authority: In many IoT scenarios, there are many devices that are operating on behalf of a user and other scenarios where a device may operate on a third party’s behalf for a specific period of time. The access control model should implement delegation of authority to provide more usability and flexibility to the IoT system [24].
- Auditability: Any and every access control needs to be auditable. Hence, collection and storage of evidence necessary for context awareness. This becomes a challenge when utilizing a distributed approach [17].
To ensure confidentiality and integrity of system resources, the access control is used to guarantee that only authorized users granted the appropriate access permissions. There are several access control models which can be divided into two classes; traditional and dynamic access control models [19].
Traditional access control approaches are based on policies that are static and rigid in nature. These policies are predefined and always give the same outcome regardless of the situation. Therefore, this static approach fails to adapt to varied and changing conditions during making access decisions [20]. There are three main traditional access control models; Discretionary Access Control (DAC), Mandatory Access Control (MAC) and Role-based Access Control (RBAC).
DAC model was designed for multi-user databases and systems with a few previously known users. All the system resources are under full control from the user. DAC grants access depending on the user identity and authorization, which is defined for open policies. The owner of the resource can grant the access to any user [19]. While MAC model is concerned with confidentiality and integrity of information, so it mainly used in military and government applications. In MAC, the security policy is controlled by a security policy administrator and the user does not have the capability to override it [19]. RBAC model is consists of three elements: users (subjects requesting access), roles (collection of permission) and operations (actions on target resource). Access permissions are related to roles and the appropriate role is granted to the user. A single user can be associated with one or more roles, and a single role can include one or more user. RBAC provides a classification of users based on their roles [21].
Dynamic access control models are characterized by using not only the access policies but also dynamic contextual features which are estimated in real-time at the time of the request [22]. These real-time features can include trust, risk, context, history and operational need [23], [14]. In this paper, we propose a risk-based access control model that uses the security risk as the main criterion for making the access permissions.
The risk can be defined as the possibility of loss or injury. Generally, the risk is about some event that may occur in the future and cause losses. One such risk is the leakage of sensitive information by users. The access control is one of the approaches used to mitigate against the security risk [27]. Risk-based access control model permits or denies access requests dynamically based on the estimated risk of each access request [20]. This model performs a risk analysis on each user access request to make the access decision [7]. Mathematically, the most common formula to represent the risk in quantitative terms is:
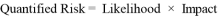                        (1)
                       (1)
Where likelihood represents the probability of an incident to happen while impact represents the estimation of the value of the damage regarding that incident [20].
Quantified risk-based access control models are divided into two types: non-adaptive and adaptive. The fundamental distinction between adaptive and non-adaptive approaches is that the adaptive model requires a system monitoring process and the risk estimation module adaptively adjusts user permissions based on the users’ activities during access sessions. While non-adaptive approach only calculates the risk during each session creation and does not have run-time monitoring and abnormality detection capability [11].
Dynamic access control approaches use real-time environment features to make the access decision. One of these features is the security risk associated with the access request, which will be used in our proposed model to make the access decision. The proposed model is shown in figure 2.
The proposed model has four inputs: user/agent context, resource sensitivity, action severity and risk history. These inputs/risk factors are used to estimate the security risk value associated with each access request. The final risk value is then compared with risk policies to make the access decision. To make the model adaptive, the user behavior is monitored to detect any abnormal actions from authorized users. This model can provide an appropriate security level while ensuring flexibility and scalability to the IoT system.
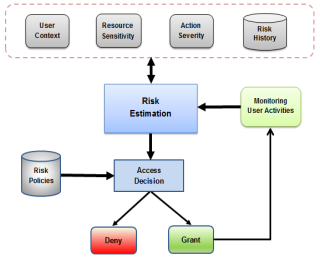
Fig. 2. The proposed adaptive risk-based access control model
As shown in figure 2, the user/agent context represents the environmental features that are embedded with the user/agent at the time of making the access request. These contexts are used to determine the security risk value associated with the user requesting the access to the system. Location and time are the most common user contexts [28]. Resource sensitivity represents how valuable the resource/data is to the owner or to the service provider. Data is assigned a level of sensitivity based on who should have access to it and how much damage would be done if it were disclosed. A risk metric is assigned to each resource in the IoT system depending on how valuable the resource data is to the owner. For instance, the higher the data sensitivity, the higher the risk metric associated with the resource. Action severity represents the consequences of a certain action on a particular resource in terms of security requirements of confidentiality, integrity, and availability. Different operations have different impacts and so have different risk values. For instance, the risk of a “view” operation is lower than the risk of a “delete” operation. The user risk history is used to estimate the risk value of each access request. This is because the risk history reflects previous users’ behavior patterns. Moreover, it is used to identify good and bad authorized users and predict the user future behavior. Risk estimation module is responsible for taking the input features to quantify the risk value that is associated with the access request. The ultimate goal is to develop an efficient risk estimation process. The access decision determines whether access is granted or denied according to the risk policies. Risk policies or access control policies are mainly used by the risk estimation module to make the access decisions. These policies are created by the resource owner to identify terms and conditions of granting or denying the access. The overall risk value is examined with the risk policies to determine the access decision.
The proposed model is trying to improve the flexibility of access control by monitoring the user behavior during the access session. In current access control models, if the decision is to grant access to the user, then there is no way to prevent any abnormal and unusual data access from the authorized user. So a monitoring module is needed to adaptively adjust the risk value based on the user behavior during the access session. Applying smart contracts to accomplish this process is a big challenge especially it will be the first time to use the smart contracts in this context. Smart contracts are treated as a software code that runs on a blockchain [29]. It can force a functional implementation of particular demands and can confirm that certain conditions or terms were met or not [30]. Hence, the monitored user behavior information will be compared with the smart contract to ensure that the user acts according to the terms of the smart contract so as to prevent any potential security breach during the access sessions.
The process flow of the proposed model is shown in figure 3. The flow starts when the access control manager receives an access request from a user. After that, the access control manager asks for the system contexts (user/agent, resource, and action) of the requested user in addition to the user risk history. The risk estimation module uses these contexts with the risk history to estimate the overall access risk value related to the requested user, then the estimated risk value is compared with risk policies to determine the access decision. At this point, we have two decisions:
a) If the access is granted, then the monitoring module will track the user behavior. The smart contract will use the monitored data to determine if the user follows the contract terms or not. If yes, then it will keep monitoring the user behavior, while if not, then it will return to the risk estimation module to reduce user permissions or terminate the access session to stop any security breach.
b) If the access is denied, then the system asks the user to provide additional proof of identification so as not to block an authorized user and reduce the false-positive rate. If the user provides the required identification, then the access is granted and the flow continues as in the first decision, while if not, the system denies the access.
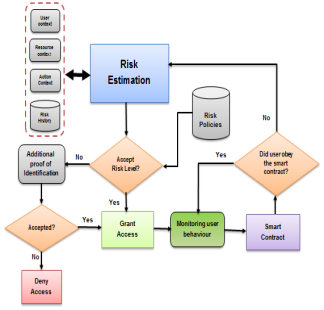
Fig. 3. The process flow of the adaptive risk-based access control model
This section provides a brief summary of the models that are related to the proposed model. A number of studies have been conducted the security risk for dynamic access control models. The JASON report [31] proposed three main elements for a risk-based access control model: estimating the risk value associated with each access request, identifying acceptance levels of risk in a certain domain, and controlling information sharing based on the estimated risk and access control policies.
Risk Adaptable Access Control (RAdAC) model has been proposed by McGraw [32]. It is based on estimating the security risk and operational needs to grant or deny the access. This model estimates the risk associated with each access request then compares it with the access control policy. After that, the system verifies the operational needs; if the associated operational needs and the policy are met then access is granted. However, the author did not provide details about how to quantitatively estimate risk and operational needs. Also, Kandala et al. [33] have provided an approach that identifies different risk components of the RAdAC model using attribute-based access control approach.
A dynamic and flexible risk-based access control model has been proposed by Diep et al. [12]. This model uses the risk assessment to estimate the risk value depending on outcomes of actions in term of availability, confidentiality, and integrity. However, this model did not provide a standard about how to evaluate the risk value for each state of the environment and for each outcome of action, did not use user context, and lacked risk adaptive features.
A framework proposed by Khambhammettu et al. [34] that based on estimating object sensitivity, subject trustworthiness, and the difference between object sensitivity and subject trustworthiness using a risk assessment. However, the model did not provide how to estimate the risk value for each situation of the environment. Besides, the model requires a system administrator to give a reasonable value for each input feature in the early state of the risk assessment process and lacked risk adaptive features.
A fuzzy Multi-Level Security (MLS) access control model has been proposed to manage risk information flows based on estimating its operational needs, risk possibility and environment features [20]. It estimates the risk based on the difference between subject security level and object security level. Similarly, Ni, Bertino, & Lobo [35] have proposed a risk-based access control model that based on fuzzy inferences. It showed that fuzzy inference is a good approach for estimating access security risks. However, both models ignored the past behavior of users in the risk estimation process, lacked risk adaptive features and time overhead of fuzzy inference system is high.
A fuzzy-based risk access control model has been proposed by J. Li, Bai, & Zaman [27] to estimate the risk of healthcare information access. A risk metric is associated with data sensitivity, action severity, and risk history as a fuzzy value to determine the appropriate control of healthcare information access in a cloud computing. However, this model did not provide how to quantitatively estimate the risk. Also, no clear risk boundaries are defined and lacked risk adaptive features.
A dynamic risk-based decision method has been proposed by Shaikh et al. [14]. This method is based on using the past behavior to identify good and bad authorized users. It depends on granting reward and penalty points to users after the completion of transactions. However, the past user behavior (reward/penalty) values are not enough to decide the access decision. Besides, no risk prediction technique is used and lacked risk adaptive features.
A risk analysis approach has been proposed by Rajbhandari & Snekkenes [36] to provide access decisions dynamically. This approach is based on preferences or values of benefit which subjects can provide rather than subjective probability using the game theory. A simple privacy scenario between a user and an online bookstore is introduced to provide an initial perception of the concept. However, using only benefits of the subject to determine the access decision is not enough to develop a flexible and scalable access control model. Also, it lacked risk adaptive features.
A task-based access control model has been proposed by Sharma et al. [37] to estimate the risk value using functions that based on the action a user wants to perform. The risk value is computed in terms of different actions and corresponding outcomes. The outcomes and the risk probability are determined along with the level of data sensitivity. The previous users’ behavior patterns are then used to estimate the overall risk value. The estimated risk value is compared with the risk threshold to determine the access decision. However, it lacked risk adaptive features.
A contextual risk-based access control model has been proposed by Lee et al. [13]. The model gathers all useful information from the environment and evaluates them from the security perspective. Risk assessment with multifactor evaluation process (MFEP) technique is applied to estimate the associated risk value. The risk value is based on outcomes of actions in term of availability, confidentiality, and integrity. This model is evaluated to manage the access control in a hospital. However, this model ignored the past user behavior and risk adaptive features as well.
A risk-based access control model has been proposed by Dos Santos et al. [7]. This model employed the notion of quantifying risk metrics and aggregating them. It is based on the idea of risk policies, which allow service providers and resource owners to define their own metrics, allowing greater flexibility to the access control system. However, this model requires a system administrator to ensure the minimum security is achieved.
Table 1 provides a summary of the related risk-based access control models. It contains the risk estimation technique used to estimate the risk value in each model, risk factors used to estimate the risk value and the limitations of each model regarding our proposed model.
In summary, one can say that the problem of the access control, especially in the IoT, needs more investigation. Current access control models concentrate only on providing access decisions without providing any way to prevent any abnormal and unusual data access from authorized users, whereas our approach is based on providing the access decision and monitoring the user behavior to detect any abnormal actions. The novelty of our approach is based on providing the adaptive features and requesting user context attributes to the risk-based access control in the IoT system. To the best of my knowledge, using smart contracts to monitor the user access behavior will be the first try.
Table 1. Some of the risk-based access control models
|
Previous work |
Risk Estimation method |
Risk factors |
Limitations |
|
[20] |
Fuzzy MLS Model |
Difference between subject security level and object security level |
The user past behavior has not been used to detect user future behavior and lacked adaptive features. |
|
[27] |
Fuzzy Model |
Data sensitivity, action severity, and user risk history |
No clear risk boundaries are defined and lacked adaptive features. |
|
[35] |
Fuzzy Inference |
Object security level and subject security level |
Time overhead of fuzzy inference is high and lacked adaptive features. |
|
[34] |
Risk Assessment |
Object sensitivity, subject trust and difference between them |
User risk history has not been used and lacked adaptive features. |
|
[14] |
Risk Assessment |
History of reward and penalty points |
Limited risk factors, no risk prediction technique is used and lacked adaptive features. |
|
[36] |
Game Theory |
Access benefits of the subject |
Limited risk factors and lacked adaptive features. |
|
[37] |
Mathematics Functions |
Data Sensitivity, action severity, and risk history |
No risk prediction technique has not been used, lacked adaptive features and user context. |
|
[13] |
Risk Assessment |
Outcomes of actions |
Limited risk factors, lacked adaptive features and user context. |
|
[12] |
Risk Assessment |
Outcomes of actions |
Limited risk factors, no risk prediction technique has been used, lacked adaptive features and user context. |
|
[7] |
Mathematics Functions |
Risk policies |
Limited risk factors and lacked adaptive features. |
The IoT has become a widely examined subject that takes the attention of many researchers, specialists, and experts. Due to the dynamic nature of the IoT, traditional access control approaches cannot provide required security levels as they are based on a static and complex authentication infrastructure. Therefore, the scope of this paper is to develop a dynamic and adaptive risk-based access control model for the IoT. This model can adapt to IoT changing conditions. The proposed model can be realized by estimating the security risk using IoT real-time features at the time of the access request to make the access decision. The model uses user context, resource sensitivity, action severity and risk history as inputs to estimate the overall risk value associated with each access request. The model provides adaptive features to monitor user behavior and prevents any misuses from authorized users using smart contracts.
The above work is still in the first stage. In future work, choosing the most appropriate risk estimation technique for a specific IoT context is our highest priority to proceed to implement the model as well as creating different IoT access control case studies with data to evaluate the model.
Acknowledgment
We acknowledge Egyptian cultural affairs and mission sector and Menoufia University for their scholarship to Hany Atlam that allows the research to be undertaken.
References
[1]S. Li, L. Da Xu, and S. Zhao, “The internet of things: a survey,” Inf. Syst. Front., vol. 17, no. 2, pp. 243-259, 2015.
[2]M. Elkhodr, S. Shahrestani, and H. Cheung, “The Internet of Things: Vision & challenges,” IEEE 2013 Tencon – Spring, TENCONSpring 2013 – Conf. Proc., pp. 218-222, 2013.
[3]K. Ashton, “That ‘Internet of Things’ Thing,” RFID J., p. 4986, 2009.
[4]ITU, “The Internet of Things,” Itu Internet Rep. 2005, p. 212, 2005.
[5]ITU, “Overview of the Internet of things,” Ser. Y Glob. Inf. infrastructure, internet Protoc. Asp. next-generation networks – Fram. Funct. Archit. Model., p. 22, 2012.
[6]K. Habib and W. Leister, “Context-Aware Authentication for the Internet of Things,” Elev. Int. Conf. Auton. Auton. Syst. fined, pp. 134-139, 2015.
[7]D. R. Dos Santos, C. M. Westphall, and C. B. Westphall, “A dynamic risk-based access control architecture for cloud computing,” IEEE/IFIP NOMS 2014 – IEEE/IFIP Netw. Oper. Manag. Symp. Manag. a Softw. Defin. World, pp. 1-9, 2014.
[8]J. Liu, Y. Xiao, and C. L. P. Chen, “Authentication and access control in the Internet of things,” Proc. – 32nd IEEE Int. Conf. Distrib. Comput. Syst. Work. ICDCSW 2012, pp. 588-592, 2012.
[9]N. Ye, Y. Zhu, R. C. Wang, R. Malekian, and Q. M. Lin, “An efficient authentication and access control scheme for perception layer of internet of things,” Appl. Math. Inf. Sci., vol. 8, no. 4, pp. 1617-1624, 2014.
[10]V. Suhendra, “A Survey on Access Control Deployment,” Commun. Comput. Inf. Sci., pp. 11-20, 2011.
[11]K. Z. Bijon, R. Krishnan, and R. Sandhu, “A framework for risk-aware role based access control,” 2013 IEEE Conf. Commun. Netw. Secur., pp. 462-469, 2013.
[12]N. N. Diep, L. X. Hung, Y. Zhung, S. Lee, Y. Lee, and H. Lee, “Enforcing Access Control Using Risk Assessment,” Fourth Eur. Conf. Univers. Multiservice Networks, pp. 419-424, 2007.
[13]S. Lee, Y. W. Lee, N. N. Diep, S. Lee, Y. Lee, and H. Lee, “Contextual Risk-based access control,” Proc. 2007 Int. Conf. Secur. Manag., p. pp 406-412, 2007.
[14]R. A. Shaikh, K. Adi, and L. Logrippo, “Dynamic risk-based decision methods for access control systems,” Comput. Secur., vol. 31, no. 4, pp. 447-464, 2012.
[15]D. Ricardo dos Santos, C. M. Westphall, and C. B. Westphall, “Risk-based Dynamic Access Control for a Highly Scalable Cloud Federation,” Proc. Seventh Int. Conf. Emerg. Secur. Information, Syst. Technol. (SECUREWARE 2013), pp. 8-13, 2013.
[16]Y. Lee, “Technology Trends of Access Control in IoT and Requirements Analysis,” IEEE, Inf. Commun. Technol. Converg. (ICTC), 2015 Int. Conf., pp. 1031-1033, 2015.
[17]M. Adda, J. Abdelaziz, H. Mcheick, and R. Saad, “Toward an Access Control Model for IOTCollab,” 6th Int. Conf. Ambient Syst. Networks Technol., vol. 52, no. Ant, pp. 428-435, 2015.
[18]J. Hernández-Ramos and A. Jara, “Distributed Capability-based Access Control for the Internet of Things,” J. Internet Serv. Inf. Secur., vol. 3, pp. 1-16, 2013.
[19]C. Langaliya and R. Aluvalu, “Enhancing Cloud Security through Access Control Models : A Survey,” Int. J. Comput. Appl., vol. 112, no. 7, pp. 8-12, 2015.
[20]P. Chen, C. Pankaj, P. A. Karger, G. M. Wagner, and A. Schuett, “Fuzzy Multi – Level Security : An Experiment on Quantified Risk – Adaptive Access Control,” 2007 IEEE Symp. Secur. Privacy(SP’07), pp. 222-227, 2007.
[21]D. F. Ferraiolo, J. a Cugini, and D. R. Kuhn, “Role-Based Access Control: Features and Motivations,” Proc. 11th Annu. Comput. Secur. Appl. Conf., pp. 241-248, 1995.
[22]Q. Wang and H. Jin, “Quantified risk-adaptive access control for patient privacy protection in health information systems,” Proc. 6th ACM Symp. Information, Comput. Commun. Secur. – ASIACCS ’11, pp. 406-410, 2011.
[23]Y. Li, H. Sun, Z. Chen, J. Ren, and H. Luo, “Using Trust and Risk in Access Control for Grid Environment,” Secur. Technol. 2008. SECTECH ’08. Int. Conf., pp. 13-16, 2008.
[24]A. Ouaddah, I. Bouij-Pasquier, A. Abou Elkalam, and A. Ait Ouahman, “Security analysis and proposal of new access control model in the Internet of Thing,” 2015 Int. Conf. Electr. Inf. Technol., pp. 30-35, 2015.
[25]P. Fremantle, B. Aziz, J. Kopecky, and P. Scott, “Federated Identity and Access Management for the Internet of Things,” 2014 Int. Work. Secur. Internet Things, no. August 2016, pp. 10-17, 2014.
[26]B. Farroha and D. Farroha, “Challenges of ‘operationalizing’ dynamic system access control: Transitioning from ABAC to RAdAC,” Syst. Conf. (SysCon), 2012 IEEE Int., pp. 1-7, 2012.
[27]J. Li, Y. Bai, and N. Zaman, “A fuzzy modeling approach for risk-based access control in eHealth cloud,” Proc. – 12th IEEE Int. Conf. Trust. Secur. Priv. Comput. Commun. Trust. 2013, pp. 17-23, 2013.
[28]C. Perera, A. Zaslavsky, P. Christen, and D. Georgakopoulos, “Context aware computing for the internet of things: A survey,” IEEE Commun. Surv. Tutorials, vol. 16, no. 1, pp. 414-454, 2014.
[29]K. Christidis and M. Devetsikiotis, “Blockchains and Smart Contracts for the Internet of Things,” IEEE Access, vol. 4, 2016.
[30]H. Watanabe, S. Fujimura, A. Nakadaira, Y. Miyazaki, A. Akutsu, and J. Kishigami, “Blockchain contract: Securing a blockchain applied to smart contracts,” 2016 IEEE Int. Conf. Consum. Electron., pp. 467-468, 2016.
[31]C. Jason, “HORIZONTAL INTEGRATION: Broader Access Models for Realizing Information Dominance,” MITRE Corp. Tech. Rep. JSR- 04-132, 2004.
[32]R. McGraw, “Risk-Adaptable Access Control ( RAdAC ),” inPrivilege Manag. Work. NIST-National Inst. Stand. Technol. Technol. Lab., 2009.
[33]S. Kandala, R. Sandhu, and V. Bhamidipati, “An Attribute Based Framework for Risk-Adaptive Access Control Models,” Proc. 6th Int. Conf. Availability, Reliab. Secur., pp. 236-241, 2011.
[34]H. Khambhammettu, S. Boulares, K. Adi, and L. Logrippo, “A framework for risk assessment in access control systems,” Comput. Secur., vol. 39, no. Sec 2012, pp. 86-103, 2013.
[35]Q. Ni, E. Bertino, and J. Lobo, “Risk-based access control systems built on fuzzy inferences,” Proc. 5th ACM Symp. Information, Comput. Commun. Secur. ser. ASIACCS 10. New York, NY, USA ACM, pp. 250-260, 2010.
[36]L. Rajbhandari and E. A. Snekkenes, “Using game theory to analyze risk to privacy: An initial insight,” Priv. Identity Manag. Life, Springer Berlin Heidelb., pp. 41-51, 2011.
[37]M. Sharma, Y. Bai, S. Chung, and L. Dai, “Using risk in access control for cloud-assisted ehealth,” High Perform. Comput. Commun. 2012 IEEE 9th Int. Conf. Embed. Softw. Syst. (HPCC-ICESS), 2012 IEEE 14th Int. Conf., pp. 1047-1052, 2012.