Secure Vehicular Traffic Re-routing System using SCMS
Secure Vehicular Traffic Re-routing System using SCMS in connected cars
ABSTRACT
The centralized system encounters two vital issues, the centralized server needs to accomplish genuine calculation and communication with the other vehicles continuously, which can make such architecture infeasible for extensive zones with various vehicles; and driver security is not guaranteed since the drivers need to share their area furthermore the beginning stages and goal of their excursion with the server, which may keep the acknowledgment of such courses of action. To address these issues, a half and half vehicular rerouting structure is enlivened. The structure off-weights a tremendous part of the rerouting figuring at the vehicles, and therefore, the re-coordinating system gets the opportunity to be useful persistently. To settle on group rerouting decisions, the vehicles exchange messages over vehicular extraordinarily delegated frameworks. The system is hybrid since notwithstanding it uses a server to choose an exact overall point of view of the development more than 2G/3G affiliation. Likewise imperative is that the customer security is balanced with the rerouting ampleness. SCMS issues advanced endorsements to taking an interest vehicles for setting up trust among other vehicle, which is imperative for prosperity applications in perspective of vehicle-to-vehicle correspondences. It underpins four principal use cases, to be particular, bootstrapping, endorsement provisioning, bad conduct reporting and renouncement. The principle outline aim is to give both security and insurance to the greatest degree sensible and possible. To fulfill the last specified, vehicles are provided pseudonym certificates, and the provisioning of those supports is partitioned among different affiliations. The essential challenges is to energize capable renouncement while giving insurance against various attacks from insiders.
Keywords
Intelligent vehicles, VANET, SCMS, IOT, P2P Communication, Traffic Re-Routing.
Traffic congestion has changed into a continually developing issue the world over. Blockage diminishes ampleness of transportation foundation and expands travel time, air pollution, and fuel utilize. Traffic blockage acknowledged urban Americans to travel 4.8 billion hours more than should be required and to buy an additional 1.9 billion gallons of fuel, for a stop up cost of $101 billion in 2010. It is normal that by 2015, this cost will scale to $133 billion (i.e., more than $900 for each expert). The measure of abused fuel will hop to 2.5 billion gallons (i.e., enough to all more than 275,000 gas tanker trucks) [1]. While blockage is, figuratively speaking, considered as a significant city issue, delays are winding up being consistently normal in negligible urban areas and some commonplace zones also. Starting now and into the foreseeable future, finding reasonable reactions for clog adjust at sensible expenses is changing into a stringent issue.
The considering is that all the more convincing vehicle re-directing can be proactively given to individual drivers accommodatingly, in light of the communitarian information amassed from shrewd mobile phones or structures presented in vehicles, to encourage the impacts of blockage in the city. The advances of the rising distinguishing and get ready pushes empowers unavoidable change of the Intelligent Transportation System (ITS). ITS arrangements to update the voyager encounter by melding advancement and data into the present transportation structure. Vehicle re-coordinating framework (VRS) progression is a subset of ITS. In the previous 30 years, assorted VRS advancements have been considered and made the world over using unmistakable courses of action to accomplish chop down travel time for drivers. At present static passed on street side sensors (e.g., acknowledgment circles, camcorders) and vehicles going about as versatile sensors (i.e., utilizing implanted vehicular frameworks or pushed cells) can collect steady information to screen the activity at fine granularity. For instance, the Mobile Millennium widen [2] demonstrated that specific a low rate of drivers need to offer information to satisfy a right activity see.
The centralized system gathers reliable development information from vehicles and conceivably street side sensors, and it completes a couple re-routing methods to delegate another course to every re-routed vehicle in light of real travel time in the street deal with. Rather than utilizing basic most short way figuring’s, the re-guiding strategies utilize stack changing heuristics to figure the new course for an offered vehicle to relieve the potential blockage and to chop down the common travelling time for all vehicles. This specialized way is pushed to a vehicle driver when indications of blockage are seen on his stream way. Regardless, paying little personality to completing a tremendous decreasing in the travel time experienced by drivers, united strategies, for example, our own specific experience the malevolent effects of two trademark issues. In the first place, the central server needs to perform honest to goodness estimation (re-route vehicles to new ways) and correspondence with the vehicles (to send the course and to get territory redesigns) incessantly continuously.
It would make centralized system infeasible for boundless districts with different vehicles. In a centralized Vehicle Re-routing framework, the server requires the steady area and moreover the starting point and goal of the vehicles to survey the activity conditions and give productive individual re-steering course. This prompts to significant security stresses toward the drivers and may keep the appointment of such blueprints in perspective of “Big Brother” fears. For whatever time span that vehicles‟ takes after are completely unveiled, client’s character can without a lot of a broaden be comprehended paying little personality to the probability that monikers utilized [3]. This is an immediate consequence of the way that territory can contain individual’s character data [4]. Besides, a movement of area tests will as time goes on reveal the vehicle’s personality [5]. In this way, it is significant to make the structure work without uncovering the customer’s Origin and destination (OD) sets and with inconsequential number of area overhauls along a client travel.
In any case, a totally decentralized outline is not sensible for a proactive re-routing system. For example, by making vehicular specially appointed systems (VANETs), the vehicles can trade information using multi-jump correspondence, and in this manner can perceive signs of blockage in little correspondence while sparing their security. In any case, VANETs don’t permit vehicles to get an exact worldwide activity perspective of the road arrange, achieving incorrectly or if nothing else minimum imperfect re-routing. In like manner, in a totally circulated plan, as a result of the nonattendance of a facilitator, the vehicles can’t take synchronized exercises meanwhile, which makes it infeasible to settle on group arranged decisions persistently. To handle each one of these issues, this article proposes DIVERT, a dispersed vehicular re-routing system for blockage evading, which impacts both cell Internet and VANET correspondence. Possess is a crossbreed system since in spite of all that it uses a server, reachable over the Internet, to choose an exact overall point of view of the movement. The consolidated server goes about as a coordinator that accumulates zone reports, recognizes movement blockage and scatters re-routing notices (i.e. overhauled travel times in the road framework) to the vehicles.
In any case, the system offloads an unlimited part of the re-routing figuring at the vehicles and consequently the re-steering process gets the opportunity to be particularly helpful dynamically. To take synergistic re-routing decisions, the vehicles orchestrated in a comparable area trade messages over VANETs. Furthermore, DIVERT executes a security change tradition to guarantee the users‟ assurance, where each vehicle recognizes the road thickness locally using VANET and furtively reports data with a particular probability just from high activity thickness lanes. Right when signs of blockage are perceived, the server sends the action framework to the vehicles that sent the latest upgrades. Thusly, these vehicles scatter the action data got from the server in their locale.
Customer security is uncommonly upgraded since this convention decreases radically the amount of vehicle area overhauls to the server and, thusly, the driver presentation and distinguishing proof dangers. Also, in this half and half plan, the server does not know the OD sets of the customers. Along these lines, the standard duty of this article is the scattered system for re-coordinating. Involve, has four crucial components: (1) a versatile structure building for appropriated re-routing, (2) dispersed re-routing estimations that use VANETs to vehicle accommodatingly enlist an individual alternative route for each vehicle that considers the incorporating vehicles‟ future ways. (3) security careful re-routing that on a very basic level decreases fragile area data presentation of the vehicles, and (4) upgrades to diminish the VANET overhead and henceforth improve vehicle-to-vehicle correspondence idleness.
Re-Routing in VANET to keep away from congestion in the versatile environment by preserving security of client.
- Centralized System is not adaptable for expanding vehicles.
- Centralized System causes danger to the client protection
- No V2V security
- Emergence of Smart City programs in India
- Building In-App versatile minimal effort navigation
- Assigning separate course to every vehicle if there should be an occurrence of re-routing when congestion happens..
- Protecting user’s privacy from server.
- Implementing security and credential management system among V2V communication
- Implementing hybrid model while communicating with server i.e. direct Vehicle- to-Server or Vehicle to RSU to Server communication.
5.1 Existing Vehicle Routing Services
Projects, for instance, Mobile Millennium [14], CarTel , JamBayes , Nericell ,and surface street estimation [4] vehicle test data accumulated from vehicle on-board GPS devices to change the state of development and gage most constrained travel time. The proposed investigate moves past this idea: instead of investigating the achievability and precision of using PDAs as action sensors, this wander focuses on using that information to recommend courses more splendidly, in this way, fulfilling better adequacy to the extent keeping up a key separation from blockage and diminishing travel time. Organizations, for instance, INRIX [3] give continuous development information at a particular passing precision, which licenses drivers to pick elective courses if they are showing lower travel times. According to Wardrop’s first action concordance standard [6], this could incite to a customer perfect development adjust. It is known, in any case, that no real adjust can be found under stop up. A couple of exercises have been take in the headings of envisioning whole deal discontinuous and transient non-tedious blockages [4]. In any case, the handiness of these applications is in like manner confined: (i) they have exact information generally about interstates and along these lines are not particularly important for city development, and (ii) they can’t keep up a key separation from stops up and, meanwhile, it is understood that no certified concordance can be found under blockage [3]. Non-repetitive blockages which address the greater part of all obstructs [8], are especially unsafe as drivers can’t use their expert travel times to oversee them.
5.2 Location Privacy Protection
There is reliably an trade-off among security and information sharing or disclosure. On the one side, the measure of the information collected particularly impacts the sufficiency of the system. Of course, information disclosure dismisses the all inclusive community’s security (e.g., region, heading). The request is the methods by which to evaluate the assurance and minimize the security spillage. Regarding the estimation, the work in explores the information spills in the question instruments of sorted out shared (P2P) obscure correspondence systems and how these breaks can be used to exchange off mystery. In the meantime, paper [14] described Self Exposure Risk Index (SERI) and External Exposure Risk Index (XERI) to assess the insurance spillage. Concerning region assurance, an unlimited variety of work spotlights on spatial covering to give k-namelessness, which guarantees a customer to be indistinct from at any rate k-1 others.
The work in battles that both spatial and common estimations should be considered in the figuring to achieve better k-mystery, where a structure is proposed to engages each versatile client to show the base level of lack of definition that it needs and the most extraordinary transient and spatial strength’s that it will recognize. Distinctive techniques can be used to fulfill impelled k-anonymity, for example, registers zone entropy while uses the prefix of the territory hash regard. To keep the zone taking after, achieves k-secrecy by implanting k-1 fake zone takes after. On an extremely essential level, k-obscurity reduces the way of the customer’s confinement, which is not material for steady region based organizations, for instance, persistent vehicle re-coordinating. The strategy in shows way perplexity approach which uses convenience desire to make a web of meeting ways, staying away from un-trusted zone based organizations from taking after customers while giving uncommonly correct constant region overhauls. A weakness careful way covering figuring is proposed in for sparing insurance in GPS takes after that can guarantee a level of security despite for customers driving in low-thickness domains.
- SCMS Manager: Ensures productive and reasonable operation of the SCMS, sets rules for checking on rowdiness and repudiation solicitations to guarantee that they are right as indicated by techniques.
- Certification Services: Provides data on which sorts of gadgets are guaranteed to get computerized testaments and indicates the affirmation procedure.
- CRL Store (CRLS): Stores and circulates CRLs. This is a basic go through capacity since CRLs are marked by the CRL Generator.
- CRL Broadcast (CRLB): Broadcasts the current CRL, might be done through Road Side Equipment (RSEs) or satellite radio framework, and so on. This is a go through capacity
- Device: An end-element gadget that sends BSMs, for instance On-Board Equipment (OBE) or After-market Safety Device (ASD).
- Device Configuration Manager (DCM): Provides confirmed data about SCMS part arrangement changes to gadgets, which may incorporate a segment changing its system address or testament, or handing-off approach choices issued by the SCMS Manager. It is likewise used to confirm the Enrollment CA that a gadget is qualified to get enlistment authentications.
- Enrollment CA (ECA): Issues enlistment endorsements, which go about as an international ID for the gadget and can be utilized to demand pen name. Diverse ECAs may issue enlistment declarations for various geographic areas, makers, or gadget sorts.
- Linkage Authority (LA): Generates linkage values, which are utilized as a part of the endorsements and bolster effective repudiation. There are two LAs in the SCMS, alluded to as LAl and LA2. The part keeps the administrator of a LA from connecting endorsements having a place with a specific gadget.
- Location Obscurer Proxy (LOP): Hides the area of the asking for gadget by changing source locations, and in this manner forestalls connecting of system locations to areas. Furthermore, when sending data to the Misbehavior Authority (MA), the LOP rearranges the reports to keep the MA from deciding the journalists’ courses.
- Misbehavior Authority (MA): Processes rowdiness reports to recognize potential bad conduct by gadgets, and if essential disavows and adds gadgets to the CRL. It likewise starts the way toward connecting a testament identifier to the relating enlistment endorsements, and adding-the enlistment authentication to an interior boycott. The MA contains three subcomponents: Internal Blacklist Manager (IBLM), which sends data required for upgrading the inner boycott to the RA; Global Detection (GD), which figures out which gadgets are making trouble; and CRL Generator (CRLG), which issues endorsement disavowal records to the outside world.
- Pseudonym CA (PCA): Issues here and now (nom de plume) to gadgets. Individual PCAs may, for instance, be constrained to a specific geographic area, a specific producer, or a kind of gadgets.
- Registration Authority (RA): Validates, procedures, and advances demands for nom de plume to PCA.
- Request Coordination (RC): Ensures that a gadget does not ask for more than one arrangement of endorsements for a given era. It facilitates exercises between various RAs, and is just required if a gadget could ask for authentications from different RAs
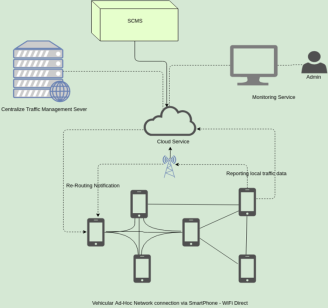
Fig. 1. System Architecture
A hybrid configuration is proposed to execute DIVERT as showed up in Figure 4.1. The building is made out of a central server and an item stack running on an on-board contraption (e.g., a propelled cell phone) in every taking an intrigue vehicle.
This structure uses two sorts of correspondence. The vehicles talk with the server over a 3/4G framework to report adjacent movement thickness data and to get the overall action thickness in the road orchestrate. The vehicles report data as showed by a security careful estimation . In like manner, the vehicles that are firmly found speak with each other over VANETs to choose the area development thickness, to scatter the movement data got from the server, and to execute a spread re-coordinating method. The server uses the vehicle action reports to gather a correct and overall point of view of the road sort out development. The framework is addressed as an organized graph where each edge looks at to a road divide. In addition, each edge has related a dynamic weight addressing the constant action thickness on the edge.
A road segment is considered to show signs of stop up when the action thickness is more conspicuous than an edge regard. Each time new road pieces give blockage suggestions, the server uploads a partly weighted diagram (i.e., simply the edges having a travel time not the same as the free stream travel time) to the cars that reported starting at late and are close to the obstruct parcels. The exhorted vehicles dissipate the information (i.e., development graph and vehicle course) in their territories with a set number of ricochets to keep up a key separation from over the top flooding. The dispersal furthermore has a timeout, which is an unfaltering parameter in the system. Exactly when the time is up, in perspective of the movement graph and course information shared by various vehicles, each vehicle, whose present way crosses the stop up spot, locally forms another course to its objective. While speaking with vehicles the vehicles affirm the mechanized verification of the get-together then simply its starts granting. Vehicles in like manner report getting acting up vehicle in structure if found, with the objective that system can affirm it and can discard its statement. Each vehicle sends underwriting when talking with the server as this can disentangle the issue of non-disavowal of message.
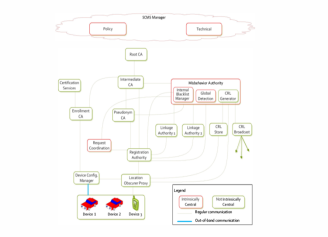
Fig.2. SCMS Architecture
- Due traffic re-routing, vehicle travel time and fuel consumption gets lowered.
- As vehicle are connected it enables other Location based service
- Traffic is controlled and managed in more efficient manner.
- It helps in traffic monitoring
- VANET-based Emergency Vehicle Warning System
- Traffic light preemption for Emergency Vehicle
- Vehicle break down notification leads to avoiding accidents
- Car Upper/Dipper alerts while turning.
- Crash avoidance
- 360 vehicle awareness.
- Intersection movement assistance.
- Do not pass warning.
- Emergency Electronic brake light warning
A feasible, cost-effective, and effective movement re-routing framework can be executed and deployed in real-time settings. This Approach is versatile as it offload the re-routing calculation on vehicle.
References
[1] D. Schrank, T. Lomax, and S. Turner. TTI’s Urban Mobility Report. Texas Transportation Institute, Texas A & M University, 2011.
[2] B. Hoh, M. Gruteser, R. Herring, J. Ban, D. Work, J.C. Herrera, A.M. Bayen, M. Annavaram, and Q. Jacobson. Virtual trip lines for distributed privacy preserving traffic monitoring. In Proceedings of the 6th international conference on Mobile systems, applications, and services, pages 15-28. ACM, 2008.
[3] Y.C. Chiu, J. Bottom, M. Mahut, A. Paz, R. Balakrishna, T. Waller, and J. Hicks. Dynamic traffic assignment: A primer. Transportation Research E-Circular, (E-C153), 2011.
[4] M. Haklay and P.Weber. Openstreetmap: User-generated street maps. IEEE Pervasive Computing, 7(4):12-18, 2008.
[5] D. Jiang and L. Delgrossi. Ieee 802.11 p: Towards an international standard for wireless access in vehicular environments. In IEEE Vehicular Technology Conference, pages 2036-2040, 2008.
[6] J.G. Wardrop. Some theoretical aspects of road traffic research. Proceedings of the Institution of Civil Engineers, Part II, 1(36):252-378, 1952.
[7] J. Kleinberg and E. Tardos. Algorithm design. Pearson Education India: Delhi, 2006
[8] Car-to-car communication.[Online; accessed on 14-Dec-2013].
[9] T. Nadeem, S. Dashtinezhad, C. Liao, and L. Iftode. Traffic view: traffic data dissemination using car-to-car communication. ACM SIGMOBILE Mobile Computing and Communications Review, 8(3):6-19, 2004.
[10] S. Dornbush and A. Joshi. Streetsmart traffic: Discovering and disseminating automobile congestion using vanets. In Vehicular Technology Conference, IEEE 65th, pages 11-15, 2007.
[11] V. Gradinescu, C. Gorgorin, R. Diaconescu, V. Cristea, and L. Iftode. Adaptive traffic lights using car-to-car communication. In Vehicular Technology Conference, IEEE 65th, pages 21-25, 2007.
[12] T. Hunter, R. Herring, P. Abbeel, and A. Bayen. Path and travel time inference from gps probe vehicle data. NIPS Workshop on Analyzing Networks and Learning with Graphs, 2009.
[13] D. Schultes. Route planning in road networks. Karlsruhe: Universitat Karlsruhe (TH) Fakultat fur Informatik. Institut fur Theoretische Informatik, Algorithmik II, 2008.
[14] N. Malviya, S. Madden, and A. Bhattacharya. A continuous query system for dynamic route planning. In Proceedings of 27th IEEE International Conference on Data Engineering (ICDE 2011), pages 792-803, 2011.
[15] N.B Taylor. CONTRAM 5, an enhanced traffic assignment model. TRRL research report. Transport and Road Research Laboratory, Crowthorne, United Kingdom, 1990
[16] J. Nzouonta, N. Rajgure, G. Wang, and C. Borcea. VANET routing on city roads using real-time vehicular traffic information. Vehicular Technology, IEEE Transactions on, 58(7):3609-3626, 2009.
[17] Juan (Susan) Pan, Iulian Sandu Popa, and Cristian Borcea DIVERT: A Distributed Vehicular Traffic Re-routing System for Congestion Avoidance. IEEE transaction in mobile computing ,2016
[18] W. Whyte, A. Weimerskirch, V. Kumar, and T. Hehn. A Security Credential Management System for V2V Communications. In Proceedings of the 2013 IEEE Vehicular Networking Conference, pages 1-8, 2013
Â
