SOAP/REST Research
Â
Web Services

Â
Over the years, along with technological evolution, software industry has adopted the concept of Web Services, defined as distributed model in which multiple web applications can intercommunicate with each other [1].
Web Services are standardized web applications that cooperate with different web applications in order to interchange information. Communication between web services is based on open protocols such as HTTP (Hypertext Transfer Protocol), WSDL (Web Service Definition Language), XML (Extensible Markup Language), SOAP (Simple Object Access Protocol), REST (Representational State Transfer), UDDI (Universal Description, Discovery, and Integration), and many more [2].
As opposed to the standard client/server model, Web Services are solely responsible for providing the business logic and transfer of data, but they do not incorporate a GUI for clients [3].
The purpose of this research paper is to evaluate, find relationships and compare two well recognized industry Web Services, namely SOAP and REST according to their architecture, functionality and security aspects.
This chapter will discuss the concept of above mentioned protocols in greater detail.
What is SOAP
SOAP is a tool that provides message-passing services with inclusion of XML protocol (messaging-layer protocol). Invented by Microsoft SOAP replaced other inefficient technologies (such as CORBA) that could not perform well over the Internet (data transmission) [4].
A great advantage of SOAP is error-reporting capability, therefore in case of request issues, appropriate response with adequate error message can be returned for the ease of debugging [4].
Interesting fact is that SOAP does not have to necessarily be used over HTTP protocol; alternatively it can be used with SMTP (Simple Mail Transfer Protocol) [4].
SOAP is wrapped with so-called ‘envelope’ (root of the SOAP message) that is used to send messages between clients and Web Services in form of requests and responses. An envelope namespace – SOAP-ENV: Envelope) is mandatory when using SOAP messages [6]. The body element of SOAP request and response include the name of the method from which the response is derived, and the schema for a package name (favouriteNumber preceded by the namespace – ns2 and MyService respectively). See figure 1 and 2 below.
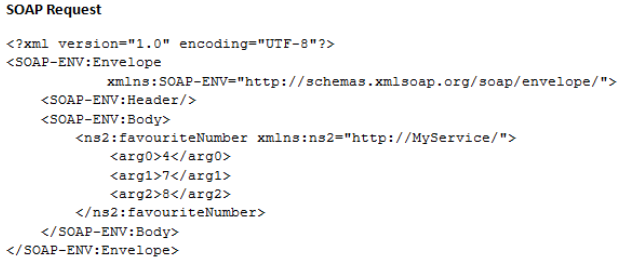
Figure 1: SOAP Request example.
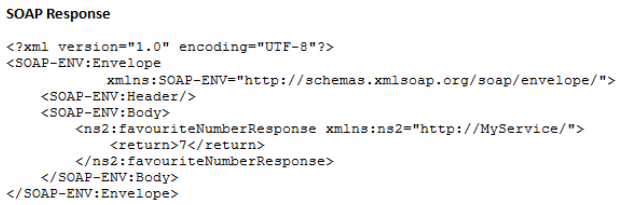
Figure 2: SOAP Response example.
SOAP services are successfully incorporated by companies like Google, eBay and Amazon.
What is REST
REST architecture has been recently preferred over the SOAP protocol as it is lighter when it comes to data transmission over the Internet. Moreover, SOAP is designed in a way that must incorporate the server and a client programs. As a result of REST being so light in communication over network, it has drawn the attention of huge corporations that implement cloud APIs and associate REST Web Services with them. Some of them are Amazon, Google, Facebook, Twitter, and Microsoft. In general REST is popular with mobile applications, automated business processes, social networking sites, etc [9]. REST Services are commonly used for Web applications where the interaction between client and service must be potentially fast.
One of the disadvantages of REST is that it is not capable of generating the client as opposed to SOAP which can achieve that through WSDL. On top of that REST utilizes messages smaller in size that SOAP, which is more efficient, saves time and money [9].
RESTful uses mapping of HTTP methods to four specific CRUD operations such as GET – to read resources, POST – to create a new resource, PUT – to create or update a resource and DELETE – to remove existing resource [6].
The idea for Web Services is to develop architectures that are easy to be scaled, extended and maintained – this is guaranteed by the RESTful architecture. RESTful design should be composed of several well-described characteristics such as representations, messages, URIs, uniform interface, stateless, links between resources and caches [6].
Messages
Messages exchanged between clients and the server contains metadata information related to the message (on top of the actual message contents) – as seen in figure 3 below.
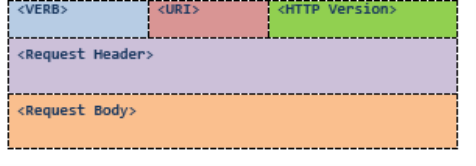
Figure 3: Rest HTTP Request format.
The ‘Verb’ segment contains one of the four HTTP methods (GET, POST, PUT, or DELETE). ‘URI’ part is the link for accessing associated resource, where the operations mentioned above can be invoked. ‘Request Header’ is comprised of information about the message and the type of client, and the ‘Request Body’ includes the message content [10].
URIs
Restful Web Services restrict to include at least one link (URI) for a resource, where undertaken action is defined and controlled by HTTP verb (as mentioned before) [10]. Example of a resource would look like this: http://www.example.com/customers.
Stateless
REST Web Service does not remember the current state of the application for its clients and therefore it can process next requests without any implications. Every next request sent by a client is performed independently from previous ones.
Caching
Cache is the feature of RESTful services that helps in storing produced results, and instead of repeating that process every time, cache uses these results if it is requested soon enough (improves performance). HTTP headers maintain caching encapsulating date and time of generated representation and its update, expiration date and the elapsed time (controlling function) [10].
Functionality
SOAP
Below described example is illustrated (simplified version) in figure 3.
Before reaching the destination, SOAP messages have to sometimes pass through numerous transport-layer protocols. The great advantage of SOAP is platform independence and programming language independence. Nearly all common and well-known languages (C++, Java, Pearl, JEE, PHP, and many more) can produce XML files to store and pass the information across different platforms. In case of usage of the HTTP protocol as a binder, a Remote Procedure Call, which is commonly used in shared networks to execute applications/services in a different address space (remotely – on another machine or in a different network) associates to an HTTP request and Remote Procedure Call response associates to an HTTP response [7].
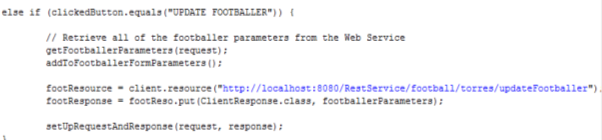
The role of a communication tool in SOAP Web Services is performed by a JAX-WS engine, which sits on a Web Service side and on a client side. Its function is to marshal (receiving objects from the Web Service client and producing SOAP request messages to be sent to the Web Service) and unmarshal transmitted SOAP messages (receiving SOAP response messages from the Web Service and producing objects which are sent back to the client) [8]. When the message is retrieved from the client, The JAX-WS tries to find the target – Implementation Class (it is a discovery process). The next step performed by the engine is to invoke a method (it is a dispatch process).
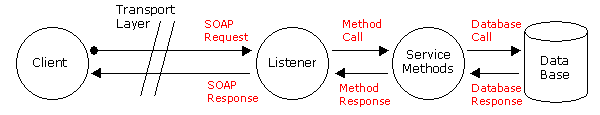
Figure 4: SOAP message passing between client and Web Service.
SOA/ROA Architecture
Software Architecture determines the system/program structures and their operations or behaviours performed in order to complete defined tasks as well as components and relationships between them. If architecture is built accurately, design risks can be detected relatively early during the SDLC (Software Development Life Cycle). Decision made on how the system is to be designed should be considered with regards to the business goals and clients’ requirements [11]. There are three commonly used request-response architectures that can be recognized in the industry such as Object-Oriented, Service-Oriented and Resource-Oriented.
SOA (Service-Oriented Architecture) is perceived as a collection of multiple services that are able to intercommunicate with each other over a network, and exchange information without any human intervention. SOA services must implicitly include service provider, someone that request the service and the tools that perform translation between them (SOAP). One of the key characteristics of SOA pertains to its loosely coupled concept, which supports enhanced reusability and provides objects independence. It also allows extending or upgrading services to satisfy business demands (great scalability). Moreover, applications can be developed using different languages and are platform independent. SOA services are described in XML documents, mainly in WSDL. SOA services are held in the registry; therefore any applications may search for and invoke desired service that is listed in the UDDI (Universal Description, Definition, and Integration) registry [12].
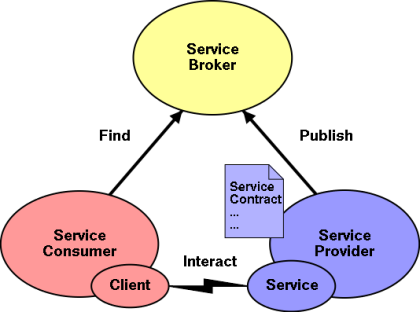
Figure 5: SOA Architecture model.
ROA (Resource-Oriented Architecture) is an architectural design that enables connection between resources (objects that are specific unique URIs).
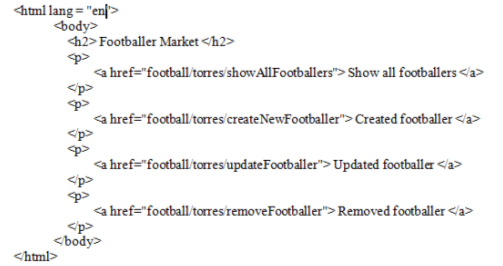
Figure 6: Rest Service index page.
The index page located in the Rest Service directory (figure 6) is linked through the hyperlink (URI) to the servlet class (figure 7 below). Each method (CRUD methods) has its own resource (hyperlink).
Figure 7: Rest client servlet class.
Representations
Resource-Oriented Architecture is focused on how to determine and enable access to objects/resources by clients (resources are accessed by URIs – web site links). These resources have to be represented within the system using different available format such as JSON or XML (XML is used for more complicated systems). It is also possible to use multiple formats for a response message when using jersey (example: @Produces ({“application/xml”, “application/json”})). The format can be chosen depending on the characteristics of clients and requests sent by clients.
Two fundamental concepts that ROA is based on are the sort of media (plain text, JSON, XML, and more) it implements and links (resources) – see the figure below.
Figure 8: Example of Media Type used by REST Web Service.
WSDL vs WADL
WSDL (We Service Description Service) is XML document (contract for SOAP Web Services) that contains abstract and concrete sections, which defines greater reusability and flexibility. Typical WSDL file includes 5 segments (3 abstract and 2 concrete elements). Those segments are: abstract – <types>, <message>, and <portType> and concrete – <binding> and <service> as illustrated in the figure below. [13]. WSDL allows for describing messages and incorporates the XML schemas (XSD) and binds specific protocols to abstract message or operation. Its role is also to define the location of the service and the methods to be invoked for that service.
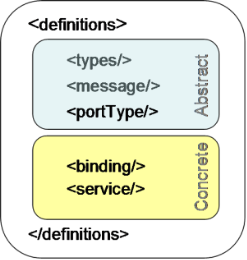
Figure 9: WSDL document main structure.
WADL (Web Application Description Language) is defined as a REST competitor to WSDL that is used by SOAP. It has the same function – support services with metadata descriptors, but it is much easier to be implemented. It is written in an XML format and includes some URIs (resources), operations and also client or service requests and responses sent back to clients or other services. The root segment (performing a function of a container) of the WADL is <application> tag. Representations are incorporated into <grammar> element and are usually associated with schemas. [13].
Web Services Security
Nowadays, the Internet is a nest of malicious activities, therefore developing secure Web Services should be at the top of the priority list. Developers should be aware of the weakest parts of the software project in order to minimise potential risks (threat model).
The main difference between SOAP and REST security is that REST derives it from the underlying transport protocol, while SOAP has to implement its own WS-Security (it is not transport dependent at all – it applies application layer security).
REST Security
REST should implement session-based authentication either through session or cookie. Authentication simply refers to verification of the user by checking credentials (username or password) to ensure that a user is what she/he claims to be. When the user is authenticated, then authorization process can be initialized, so user can be assigned explicit roles and permissions that allows for performing some operations for example CRUD methods (creating, reading, deleting and updating files).
RESTful services can be authenticated according to the four most popular methods like Basic Authentication, Digest Authentication, Certification or API Keys [14].
Basic Authentication is the most commonly used way of authenticating users, but it is the least secure, as the password and username are sent over network in plain text (they are encoded with Base64, but no encryption is involved). Due to the fact that Basic Authentication is not encrypted, the best approach is to interleave it with HTTPS protocol (HTTP over SSL which is entirely secure).
Another popular authentication method is Digest Authentication, which applies hashing algorithms like for example MD5, SHA, BCrypt to encrypt the password before it is sent to the server [14].
Client Cert Authentication requires both client and server to make agreement with the help of certificate, which must be first signed by a special agency that states the certificate is valid and legal. As opposed to the previous methods, where users send their credentials to the server, with Client Cert Authentication they send certificate. Information included in the certificate such as security credentials and public-private key are checked by the server and based on that client can be granted access to the resources or not [14].
This method must explicitly use HTTPS protocol.
Optional way of user identification is the use of API key with API secret, which are quite long randomly chosen strings. Those strings are verified by the server, which sends the respond back to the client [14].
When developing RESTful Web Services, it has to be considered to conform to some general best security practices. It is advised to always use HTTPS communication protocol to ensure constant encryption. User passwords or API keys should not be also sent as query parameters because they are visible in the browser URL, so they can be stolen and used against the user will. The strongest and most detail validation should also take place when developing REST Web Services [14].
SOAP Security
SOAP communication is more likely to be secured with SSL protocol. SOAP benefits from XML-Encryption, XML-Signature and SAML standard (Security Assertion Markup Language).
XML-Encryption is recommended by W3C and defines how the XML documents can be encrypted without being easily read or corrupted during transmission over the network. As well as XML-Signature, XML-Enc also uses KeyInfo component which delivers information to the destination about how to verify a signature or decrypted sent data. To apply the XML-Encryption, the <EncryptedData> tag is included in the XML document, and moreover, nesting this tag within the same document increment security as encryption is implemented several times [15].
One of the unique methods of authentication and authorization applied by SOAP is SAML token. This approach does not require the user to type in a password as it is based on the trust; the only one thing that is used for authentication is the user’s id. From the perspective of the user, this system can be perceived as less annoying, as once the user is authenticated it can access other services associated with the main service, without additional authentication procedures (id that was used for the first authentication is trusted and then used automatically for extra services as the case may be) [15]. See figure 10 below.
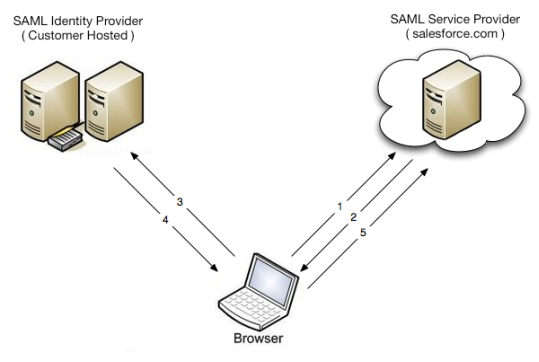
Figure 10: SAML flow example [15].
Taking into account that SOAP is extremely secure (it introduces its own WS-Security on top of SSL protocol) it is preferred over REST to implement this structure when developing bank-related web applications and services.
In general there is no optimal choice for using specific Web Services. There is an opportunity to merge protocols together if there are several service providers available (such as SOAP, REST and JASON used in one application) [5].
REST proves to be a decent option for developing Web Services that are lightweight in their nature, and can be easily detected by using resources/URIs. It is also more beneficial when it comes to complexity and usability of different forms of data that can be processed (as opposed to SOAP which can only accept XML format).
Conducting this research has given the researcher much better understanding of two main Web Service standards (SOAP and REST), and allowed extending knowledge about relationships and differences between them.
[1] “Web Services Now and When – InternetNews.”, Internetnews.com, 29 November 2004 [Online]. Available: http://www.internetnews.com/dev-news/article.php/10792_3441211_2/Web+Services+Now+and+When.htm. [Accessed: 24- Mar- 2017].
[2] “Web Services Protocol Stack”, Docs.embarcadero.com, 2008. [Online]. Available: http://docs.embarcadero.com/products/rad_studio/radstudio2007/RS2007_helpupdates/HUpdate3/EN/html/devnet/webservicesprotocol_xml.html#. [Accessed: 24- Mar- 2017].
[3] V. Beal, “What are Web Services? Webopedia Definition”, Webopedia.com, 2017. [Online]. Available: http://www.webopedia.com/TERM/W/Web_Services.html. [Accessed: 24- Mar- 2017].
[4] J. Mueller, “Understanding SOAP and REST Basics And Differences”, Blog.smartbear.com, 8 January 2013. [Online]. Available: http://blog.smartbear.com/apis/understanding-soap-and-rest-basics/. [Accessed: 24- Mar- 2017].
[5] Douglas J Barry, “Web Services Explained”, Service Architecture, 2017. [Online]. Available: http://www.service-architecture.com/articles/web-services/web_services_explained.html. [Accessed: 24- Mar- 2017].
[6] Leonard Richardson, Sam Ruby, “Web Services for the Real World”, 1st ed. Indianapolis, Sebastopol: O’Reilly Media, May 2007.
[7] I. Nandrajog, “Simplified Object Access Protocol”, Web.njit.edu, 2001. [Online]. Available: https://web.njit.edu/~turoff/coursenotes/IS679/sample/soap.htm. [Accessed: 24- Mar- 2017].
[8] “Functionality of SOAP Web services”, Itdoc.hitachi.co.jp, 2013. [Online]. Available: http://itdoc.hitachi.co.jp/manuals/3020/30203Y2310e/EY230011.HTM. [Accessed: 24- Mar- 2017].
[9] M. Rouse, “What is REST (representational state transfer)? – Definition from WhatIs.com”, SearchMicroservices, December 2014. [Online]. Available: http://searchmicroservices.techtarget.com/definition/REST-representational-state-transfer. [Accessed: 24- Mar- 2017].
[10] M. Vaqqas, “RESTful Web Services: A Tutorial”, Dr. Dobb’s, 23 September 2014. [Online]. Available: http://www.drdobbs.com/web-development/restful-web-services-a-tutorial/240169069. [Accessed: 24- Mar- 2017].
[11] “Software Architecture | Overview”, Sei.cmu.edu, 2017. [Online]. Available: http://www.sei.cmu.edu/architecture/. [Accessed: 24- Mar- 2017].
[12] R. Kodali, “What is service-oriented architecture?”, JavaWorld, 13 June 2005. [Online]. Available: http://www.javaworld.com/article/2071889/soa/what-is-service-oriented-architecture.html. [Accessed: 24- Mar- 2017].
[13] B. Spies, “Web Services, Part 2: WSDL and WADL | Ajaxonomy”, Ajaxonomy.com, 4 June 2008. [Online]. Available: http://www.ajaxonomy.com/2008/xml/web-services-part-2-wsdl-and-wadl. [Accessed: 24- Mar- 2017].
[14] L. Gupta, “RESTful Web Services Security Guide – HowToDoInJava”, HowToDoInJava, March 2016. [Online]. Available: http://howtodoinjava.com/security/restful-web-services-security-guide/. [Accessed: 24- Mar- 2017].
[15] P. Bruce, “API Security in REST vs SOAP”, Blog.smartbear.com, 29 May 2015. [Online]. Available: http://blog.smartbear.com/security/api-security-in-rest-vs-soap/. [Accessed: 24- Mar- 2017].