Strategies for Password Cracking
The aim of my project is to give ICT students an idea of the mechanism of cracking password using an using John the ripper. I will also explain the process that the application does to crack a password. Moreover,I will talk about password complexity. how does the complexity increase the cracking time? are there intractable passwords? why? encryptions . Finally , I will explain different types of cracking like brute force, dictionary attack etc.
Password cracking is one of the oldest hacking arts. Every system must store passwords somewhere in order to authenticate users. However, in order to protect these passwords from being stolen, they are encrypted. Password cracking is the art of decrypting the passwords in order to recover them.” Passwords are the most common means of authentication. Passwords are protected by using one-way cryptographic algorithms that produce a hash of set length. Cryptography can only protect something to the point where the only feasible attack on the encrypted secret is to try and guess it. However, in the case of passwords guessing is easy. Passwords are insecure by nature because they are used for preventing humans from guessing a small secret created by humans.
To understand how to get a good understanding about password, we have to understand how they are stored in a system. To store a password in a text form is strongly unacceptable. The same thing when storing the passwords deep in tree of directories that would result in “Security through Obscurity” and this is also unacceptable. Unix management file system gives an acceptable solution: one of the main distributions of Multicast (the precursor to Unix) stored the file of password in a clear text, but it can be seen by a super user only. This was a improper solution. Also caused a bug to which switching some temporary file and showed the password in text being printed for all the clients when they login.
Unix instead of doing that, saves the passwords that were hashed in the password file and not the actual passwords. After that, as the user puts his password , the system has the ability to simply compare the hash of the user password input and it will be compared with the stored hash value [1].
3.1 What a complex password should include.
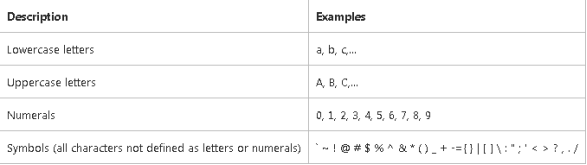
Figure 1 what password combination should include.
A strong password should include what is listed in Fig1 in order to be complex password. so, what complex password means that password that include :Upper lower case letters, symbols and numbers getting that password is an extreme power consumption and time wasting for any password cracker [2].
3.2 Common passwords
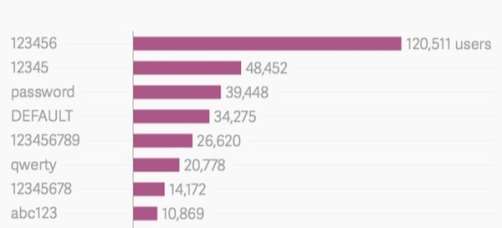
Figure 2 : the most common passwords
According to a study that was accomplished by David Bisson in 2014 . The result shows the most common passwords that are used on the Internet which any cracker would definitely add to his word list. These are typical example of an obvious passwords and easy to crack unfortunately. Easy passwords like what is shown above is very easy to guess it would not even use processor of the cracker it will be in his word list, because these passwords are the most common passwords at all time. So, any password cracker would definitely start cracking the password with guessing such passwords [3].
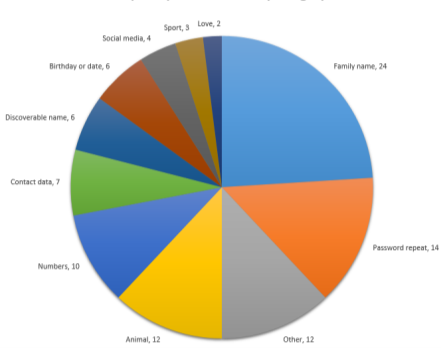
Figure 3: TOP 100 password hints by category [4]
Fig3 shows the result of a study that was done by Troyhunt shows how people choose their password.
Guessing a password from the E-mail address:
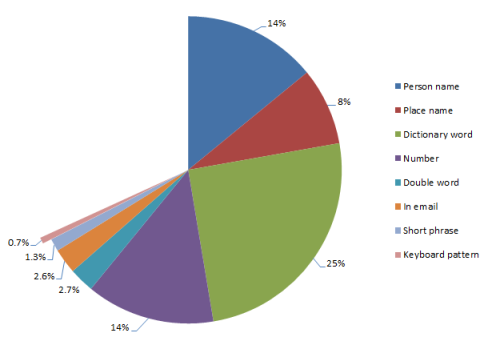
Figure 4: Passwords derived from the email address [4]
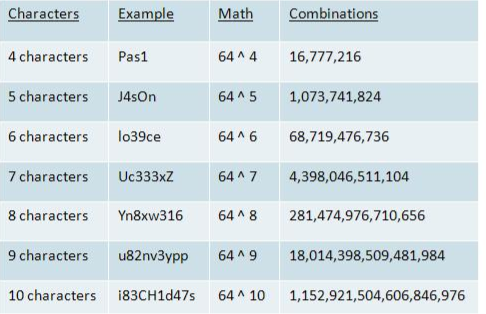
Figure 5: Number of Password combinations alphanumeric Password [5]
The table above shows number of possibilities based on the password length so, any digit of the password is considered as process loop. Each digit can have 64^ the number of digits. Imagine having 13 characters that 64 raised to the power of 13 its an extremely big number of combination that the cracker has to try. It’s extreme based on the source of the cracker processor and it’s also based on time.
3.3 Password complexity and Time
Complex password is extremely important for securing your data and information. Most of the people think their password is being hacked or sniffed but the main reason for their password was not complex so, the depending on the assigned password the time will be proportional for example, three digit numeral or alphabet password ahc, 897, or even abc432 would take less than a second for cracking. However,”[email protected]” would take almost a month to be cracked, because the cracking cycle will go checking numbers,alphabet,and symbols and that is why complex password is strongly required [6].
The quicker your PC can hash passwords, the more you can crack in a given certain of time, and that results in a better chance of having of cracked passwords. We used John The Ripper because it is an open source cracking tool which is available on almost all Linux distros. However, it is not usually the best choice. John runs depending upon the CPU, but password hashing can be launched really efficiently depending upon graphics cards. Hashcat is password cracking tool that can run on graphics cards, and on the right hardware can do much better than John. Password cracking computers most of the time have number high-performance GPUs and depend on these for their rapidity . You might not find Hashcat in your distro’s repositories, but it’s downloadable on www.hashcat. net (it’sfree as in zero cost, but not free as in free software) [7].
5.1 Cracking tools and applications
5.1.1 Aircrack-ng
it’s a free network hacking tool which include packet sniffer,detector, and various of encryption types cracker. Moreover, it includes Analysis tool that works with WLAN. In addition, this tool can sniff and monitor packets which travels from one person to another. This tool can run in a verity of platforms eg, FreeBSD, OSX, Wubdows, OpenBSD and Linux. Maemo, Zaurus and Android platforms
5.1.2 Crow bar
This tool is exclusive on Linux operating systems. It is a free tool that runs a type of password cracking technique called Brute Force. It doesn’t save a list of passwords, but try every possible combination of a password. this tool is supporting remote Desktop Protocol with NLA, VNC key authentication, open VPN and SSH private key authentication.
5.1.3 L0phtCrack
This is a recovery password auditing app designed by Mudge. It was written to crack windows encrypted passwords. Moreover, it can crack from Primary domain controllers, and network servers or Active Directory. It also allows the user to sniff a password off the wire. This tool can go further and create many methods for guessing a password. It can work only on Microsoft Windows OS.
5.1.4 Medusa
It a tool that is designed to be a strong, fast login using brute force. The purpose of this tool is to work with a lot of services remotely at the same time. That means this tool can not only brut force only one host but multiple hosts and passwords at a time. The targeted information can be registered in different methods. So each entry can be single information or file with many entries.Each mod file is for separate mod file . Meaning , this is needed for brute forcing. It is a free tool and Medusa works on Linux and MAC OS X operating systems.
5.1.5 Ophcrack
This is a rainbow table that discovers passwords and crack a complex passwords. Moreover, it can crack simple passwords within minutes.In order to get the great advantage of this tool the user has to buy what is so-called rainbow tables to crack complex passwords.This tool is free runs on Linux,Microsoft Windows and MAC operating system.
5.1.6 RainBow Crack
This tool is free and runs on Linux,Microsoft Windows, and MAC OS. It is specialized in hash cracking . It is a common brute force cracking tool that tries every combination of plaintext and that results in time consuming for complex passwords. It does not only crack passwords only but store the result in a library called(Rainbow tables).The brute force process takes extremely long time to be done but when using precompute tables it is one of the fastest cracking tool.
5.1.7 SolarWinds
This tool works on Windows only .It is also known as FireWall Security Manager. It is the best solution for any company that needs reports and advanced management on their sensitive devices. It can be configured to allow multiple clients to be deployed at Multiple system administrators at once. It also features network discovery router password decryption , SNMP brute force cracker and TCP connection reset application.
5.1.8 THC hydra
This tool is free and works on all the operating systems except MAC. This tool allows the user to remotely break into a system and crack a password using different protocols. It crack using fifty protocols. it can crack a network login. it crack the password using the dictionary or brute force attacks. It also features login brute force attack.
5.1.9 Wfuzz
This is a free tool that works on Linux Windows and Mac Os. it features the following :multiple injection points capability, recrusion when doing dictionary brute force, Post headers and authentication data brute force, out put to HTML, Proxy and SOCK support. It is usually used to brute force web applications and to find user name and password [8] [9].
6.1 Overview
John the ripper is the best cracking tool ever. John the ripper comes with two versions the popular version is free and there is a pro version which is commercial version. It runs on many platforms like DOS, Unix, BeOS, Win32 and OpenVMS. It is similar to THChydra but the main difference is that Hydra is Online password cracker whereas John the ripper is offline password cracker. It is usually used by hacktivists for penetrating passwords. John the Ripper is a fast password cracker. Period. In fact, you can consider John The Ripper as ‘the definitive’ password hacking tool.
Johnny is a graphical interface that can replace John the ripper to simplify the cracking process instead of using the command line interface. it comes by default with kali Linux.
6.2 John the ripper features
- Decrypt most guessing hashes using wordlist dictionaries.
- Ability to specify guessing with certain letters and symbols assigned by the user without using the dictionary.
- Ability to decrypt more than hash at once.
- Automatically detect the type of the hash.
- Rapidly crack passwords.
- ability to continue guessing process that has started earlier from another device [10] [11].
6.3 How does John the ripper work?
John the ripper cracks the password in four main Modes:
6.3.1 WordList Mode
It’s the simplest technique that mainly allows the user to assign what is so-called “word lists “which is a text file includes a password in each line and some password files. Also features the ability of generating other likely password files.
6.3.2 Single Crack Mode
this is the mode a user should start cracking with. It assigns the login names. Moreover, it uses GECOS which contain personal information about the user, user home dictionary, also several of rules applied. It also have got the ability to crack other password hashes if guessing is success, it would try the same password for all the hashes because more likely there will be another user with the same password. Usually the administrator should have an access to the a file which contains the users information and passwords. Finally, single mode is much faster because it cracks single password at a time. The user can also use this mode in two different files at the same time [12].
6.3.3 External Mode
To define an external cracking mode you need to create a configuration file section called [List.External:MODE], where MODE is any name that you assign to the mode. The section should contain some functions programmed in a C-like language. John will compile and use the functions if you enable this cracking mode via the command line
6.3.4 Incremental Mode.
This is the most effective and powerful cracking mode. It assigns every possible combination of characters for cracking passwords . but it still have a disadvantage which is the cracking process will keep running and will never stop because the tried combination password characters are too large. there for, crackers usually limit the character combinations to lower case so, it doesn’t take as much time as if it’s not set. It uses what is so-called”trigraph” process for example:
(aa, ab,ac,etc,), (ba,bc,bd,be,baa,bba etc,) it would not miss any password combination every combination will be tried. Its main advantage is to crack a password in a limited time [11] [10].
7.1 Brute force attack
This technique of password attack That is not actually decrypt any data, but also continue trying a list of password combination eg, words, letters .A simple brute force could be dictionary of all words commn passwords. doing trying cycle until it gets the access to an account. the complex example of brute force is trying every possible combinations of numbers, letters and symbols. However, this technique is the has to be the last option for any cracker because it can take long and the bigger number of encryption (64-32-265)bit the longer time it will take for cracking.
7.2 Dictionary attack
This type of password where the cracker can assume the password consisting of string of words, Years, or special number that is chosen from the dictionary. This tool has to be included with what is so-called dictionary input list. The cracker can download a big database including specific vocabularies for example, Sports, movies, and so on.
7.3 Password sniffing
This technique called sniff because the the crackers have the ability to sniff the authentication packets that are travelling from the client to the server among the Internet or the local area network. This technique can provide the cracker with hashes or other authentication data necessary for cracking process. There are verity of sniffers tools such as Wireshark,ScoopLM,KerbCrack. The NTLNv2 authentication traffic cannot be sniffed neither by ScoopLM nor Kerbcrack.
7.4 Password capturing
Alot of crackers get passwords easily by launching a keyboard sniffing Trojan horse or buying a physical keyboard logging device.According to many reports 82% of the most widely used viruses steal critical data.Most of them sniff passwords. Less than a $100 anyone can get key logging device which is very small and can simply fit between the keyboard and the computer’s keyboard port. It’s also extremely easy to sniff password even from wireless keyboards [13].
To conclude, First, There are verity of applications and tools that you could crack any password. Second, protecting your password requires using strong password. Moreover, there is nothing called uncrackable password its just a matter of time and resources. Finally, the only thing you can do is using strong password and keep changing your password from time to time.
[1]M. Tokutomi and S. Martin, “Password Cracking.”
[2]Chit Ko Ko Win, “Password management for you,” 08:57:17 UTC.
[3]D. Bisson, “Cracked Ashley Madison passwords consistent with years of poor security,” Graham Cluley, 16-Sep-2015. .
[4]”The science of password selection,” Troy Hunt, 17-Jul-2011. [Online]. Available: https://www.troyhunt.com/science-of-password-selection/. [Accessed: 16-Feb-2017].
[5]jsheehan2014, “Choosing a Password: Needle in a Haystack,” MACED Tech Resource, 15-May-2015. .
[6]”How Long Would it Take to Crack Your Password? Find Out! – Randomize,” Random ize. [Online]. Available: http://random-ize.com/how-long-to-hack-pass/. [Accessed: 15-Feb-2017].
[7]B. Evard, “JOHN THE RIPPER,” linuxvoice, 2015. [Online]. Available: https://www.linuxvoice.com/issues/008/john.pdf. [Accessed: 13-Feb-2017].
[8]”Wfuzz,” Concise Courses. .
[9]”10 Most Popular Password Cracking Tools,” InfoSec Resources, 27-Dec-2016. [Online]. Available: http://resources.infosecinstitute.com/10-popular-password-cracking-tools/. [Accessed: 27-Feb-2017].
[10]ports, “John the Ripper,” 18-Feb-2014. [Online]. Available: http://tools.kali.org/password-attacks/john. [Accessed: 19-Feb-2017].
[11]”John the Ripper – cracking modes,” openwall. [Online]. Available: http://www.openwall.com/john/doc/MODES.shtml. [Accessed: 20-Feb-2017].
[12]”passwords – What exactly is ‘single’ mode in John the Ripper doing?,” Information Security Stack Exchange, 2014. [Online]. Available: https://security.stackexchange.com/questions/37072/what-exactly-is-single-mode-in-john-the-ripper-doing. [Accessed: 20-Feb-2017].
[13]”Types of Password Attacks,” windowsitpro, 30-Jan-2006. [Online]. Available: http://windowsitpro.com/security/types-password-attacks. [Accessed: 02-Mar-2017].