Techniques and Types of Jailbreak
Jailbreak
Supervisor:George, Violettas
Mohammad Alfaifi
[]
[Submission Date]
Table of Contents
ABSTRACT…………………………………………………
1.Introduction……………………………………………..
1.1.Is jailbreaking legal?…………………………………..
2.Jailbreak………………………………………………..
2.1.Jailbreak types……………………………………….
2.1.1.Tethered…………………………………………
2.1.2.Semi Tethered…………………………………….
2.1.3.Untethered……………………………………….
2.2.Jailbreak teams………………………………………
2.3.How jailbreak works…………………………………..
2.4.Advantages of using jailbreak…………………………..
2.5.Disadvantages of using jailbreak………………………..
2.6.Risks of using Jailbreak………………………………..
3.Installing jailbreak………………………………………..
3.1.How to know if your device can jailbreak………………….
3.2.How to install jailbreak…………………………………
4.Cydia…………………………………………………..
4.1.History of Cydia………………………………………
4.2.Add or remove sources………………………………..
5.security…………………………………………………
5.1.Security without jailbreak………………………………
5.2.Security with jailbreak…………………………………
6.List of references…………………………………………
Apple is a global company that produces devices such as iPhone, iPad, and iMac. Actually, it is specializing in Software and they have a system called IOS. With the technology evolution, hackers have advanced and find vulnerability in Apple software that allowed breaking the system. This way called jailbreak.
This project includes a general review about jailbreak and the way it works. Also its development over the years and mention names of some organizations such as iPhone Dev team, Chronic-Dev, dream team, Pangu, Evad3rs, PP25 and Keen.
Jailbreak is one of the words that grown fast recently. Apple prefers to design something and tell you, “This is how it should be used.” Apple came with the system that is fixed which mean you are not allowed to install tools that’s help you with your needs and because of that Apple is one of a biggest secure system in the world. Some people feel that they can’t do whatever they want with feeling that Apple’s operate system is like a jail. Jailbreak came to gives the people ability to break the operating system to do whatever they want whether to install tools or themes. Apple products are well-made but they had limitation. Jailbreaking breaks those limits and gives you more control in your device.
1.1. Is jailbreaking legal?
United States of America has a rule that allowing the jailbreak and you can jailbreaking your smartphone or tablets you want[1]. Apple support center [2] published a clearance that jailbreak is legal but you will lose the support (warranty). If you install jailbreak in your Apple product, Apple will not sue you because of that and all what they can do is to stop supporting your device and if something happens it is under your responsibility.
2.1. Jailbreak types
2.1.1. Tethered
In this type, Jailbreak is temporary. When you turn off your device you can’t boot your device up without connect it to PC to delete the Jailbreak and then you are able to boot the device. In this Jailbreak you have to install it every time you turn off your device [3].
2.1.2. Semi Tethered
It looks like tethered jailbreak with addition thing that here you can turn off your device and boot it again without any problem. The features are limited [3].
2.1.3. Untethered
It is the common jailbreak and the new one. It gives the user ability to run all the tools and applications they downloaded anytime they want. In this type, you can turn off your device without fear of losing the jailbreak [3].
2.2. Jailbreak teams
There are many developers of a jailbreak, Cydia, and hackers of IOS system who have a wide fame in the community of iOS users and jailbreak system. These developers and hackers have great merit in making jailbreak a strong community. They have begun attacking the iOS system and deployment jailbreak since the early days of the issued of the first system for the iPhone. In July 2007, a few days after the release the iPhone system, a group of developers create the first tool of jailbreak, and shortly afterwards, there were many versions of tools for jailbreak. In the October 2007, they created the first jailbreak 1.0 which was also called (AppSnapp)
2.3. How jailbreak works
2.3.1. bootchain
The bootchain [4] (also called chain of trust) is the system by Apple which can tries to ensure that only signed or trusted code is loaded on an iOS device.
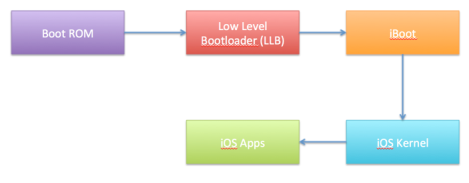
Figure 1: bootchain modulers
The bootchain consist couple of deferent modules that load each other and between the loadings there are check points that Apple put it in order to prevent unauthorized access to the code.
- Boot ROM is the first significant code that starts in the device. It is read-only which means it can’t be modified by Apple when they release a device. This part is hard to Jailbreak because it connect with the hardware not the software it in the chip inside the device, but if someone Jailbreak this part, Apple can’t stop the Jailbreak and they have to change the hardware next time they publish a new device.
- Low level Bootloader (LLB) which is a part of the software. It runs several setup routines. On firmware versions 2.0 and higher it checks the signature of Boot ROM before jumping to it. If someone found vulnerabilities and Jailbreak this part, Apple can close the vulnerabilities by releasing new software version (iOS firmware).
- iBoot is Apple’s stage 2 bootloader for all of the devices. It runs what is known as Recovery Mode. It has an interactive interface which can be used over USB or serial.
- IOS Kernel is using page verification. When you start application the Kernel will verify if the application has the code singing in tagged. If it has “SHA1” verification it will pass the application to AMFI which is a Kernel extension. The Kernel doesn’t verify if the application’s signature is valid, it is only verified if the signature is exist.
- IOS apps are the phase after the Kernel boot. It goes hand to and with iOS Kernel. For iOS all applications have to be signed since the launch of the App Store (iOS 2.0), this includes all system binaries that come with iOS. For the end user. This code signing enforcement cannot be disabled, which makes that an end user can only install applications from the App Store.
/private/etc/fstabis is where all the iOS files are stores and must be patched. fstab is like a switch that is giving you the ability to control the media partitions and the permissions. By default, fstab is setting as a read-only mode that letting you to read or view only without making any changes. To be able to make any modifications, you have to set the fstab as “read-write” mode. It is very important for your Apple device because it is controlling the permission of the media partition and the root.
The big problem is to pass in all the files you need through the various checkpoints. The checkpoint is what Apple does in order to ensuring the file is legit or coming from a third party. Every file is signed by a key. The file will be through a way and be unusable if this file without kay.
In short, we can access to the door if we either find a back door entry (bypass) or unlock the lock (patch all checkpoints). Patching is a difficult and mostly not worth the effort. So, most people who make the jailbreak will try to find a backdoor entry or a bypass.
2.3.2. Limera1n Exploit
The limera1n exploit is the bootrom and iBoot exploit used to run unsigned code (and thereby jailbreak) the iPod touch 3rd Generation, the iPhone 3GS and all A4 chip devices. It was first used in the limera1n tool by “geohot”. It is used to perform a tethered jailbreak on the devices that mentioned above. The jailbreak can then be turned into an untethered jailbreak with other exploits, such as the 0x24000 Segment Overflow [5]. Limera1n is the final publicly disclosed bootrom exploit of any device. The last device released vulnerable to limera1n is the iPhone 4.
2.4. Advantages of using jailbreak
Jailbreak means that the user can download applications without the need of Apple store, and controls the tones and add modifications to the system. Also decoding constraint on company communications device, such as AT & T or Verizon, it can go further than this when some people want to amendment on the phone. The majority is in the process of jailbreak for your iPhone, using Cydia to download the software tools to your device and install them. Cydia is an application or store tools allows owners devices that have been untying them to browse the applications and tools and carry it to the device without any restrictions
2.5. Disadvantages of using jailbreak
There are many people prefer to stay away of Jailbreak their devices. When you Jailbreak your device that means your device is no longer under the Apple ensuring [2]. All tools and applications you download are not licensed by Apple and it may break your device because it is not secure. Also one of important things in the device is the battery. Jailbreak consumes a lot of power on your device which mean your battery couldn’t stand long.
2.6. Risks of using Jailbreak
Since jailbreaking a device bypasses all security measures of the device to allow developers and users more control over the applications and device respectively, it brings inherent risks which must not be ignored by both developers and users. Here are few dangers of jailbreaking a device [3]
- Many a times jailbreaking tools installs an SSH application by default on a device and default password for iOS device alpine is very well known. If a user does not change the default password, attackers can remotely control the operation of device.
- Since jailbreaking grants root access to any application running on a device, there is a risk of malicious application accessing sensitive information of other apps.
3.1. How to know if your device can jailbreak
As a first step you have to know the version of your IOS system. Then search on Internet if this version has a Jailbreak or not. The best way to search is to get into the Jailbreak teams websites. Since Jailbreak is published by one team other teams published their copies too.
All jailbreaking tools available to install in application called Cydia, which is similar to the Apple App Store but applications available on Cydia are not checked by Apple and developers can submit their applications to distribute through Cydia.
Figure 2: Jailbroken IPhone with Cydia
4.1. History of Cydia
Cydia is a third-party installer application for all Apple devices. Developed by Jay Freeman (Saurik), Cydia is similar to the official App Store. Cydia is a manager mobile application for IOS, which enables the user to find and install tools or software packages on jailbroken device. It’s important for you to jailbreak your IOS device to get the Cydia. With Cydia everyone has the option of customizing their devices [6].
4.2. Add or remove sources
Cydia is a store depends on the developers. The sources are small stores of the developers to upload their tools on it. Cydia came within BigBoss source. This source is built-in the Cydia because it is by the Cydia creator. If you want to install other developers’ sources follow these steps:

Figure 3: iPhone Home Screen
- Find the Cydia application on your iPhone’s home screen and click on it.
Figure 4: Cydia Screen
- Click on “Sources” in the bottom bar.
- The screen of the sources that been added shown. Click on “edit” and then “add”.
Figure 5: Adding source screen
- Write the URL of the source and click on “Add Source”.
Now the source will be add into your list of sources and can search on any tool in it and install whatever you want.
5.1. Security without jailbreak
The security without Jailbreak is under Apple control. Apple has a store includes more than 2 million of applications [7]. These applications are not only for smartphones only. They support tablets, Apple TV and smart watches. Apple takes two days to approval a new application that uploaded from a developer [8]. These two days is giving Apple a time to review the app submitted to the App Store to determine whether it is perform as expected, reliable and is free of offensive material. Apple reviews every app submitted based on a set of technical, content, and design criteria.
5.2. Security with jailbreak
We agree Jailbreak is a risk for your device. This is for people with no knowledge of technologies. Privacy is one of those things that most people will say they care about, but they really don’t. However, if you truly do care about your privacy, device jailbreaking is a good way for that. Jailbreak is giving you tools to hide your information of others, even of Apple. There is another tool take care of your phone when it is stolen. When the criminal enter wrong password the tool take a selfie (photo from front camera) and send it to your E-mail with the location. Those are simples of thousands of tools give you a security more than device without Jailbreak [9].
[1]L. of C. U.S. Copyright Office, “Exemption to Prohibition on Circumvention of Copyright Protection Systems for Access Control Technologies.” U.S. Copyright Office, Library of Congress., 28-Oct-2015.
[2]”Unauthorized modification of iOS can cause security vulnerabilities, instability, shortened battery life, and other issues,” Apple Support. [Online]. Available: https://support.apple.com/en-sa/HT201954. [Accessed: 14-Jan-2017].
[3]R. Patel, “Improving Security in Jailbroken iOS Devices,” B. Thomas Golisano College of Computing and Information Sciences, Rochester, New York, 2016.
[4]Apple, “iOS Security.” May-2016.
[5]D. Keuper, “XNU: a security evaluation,” University of Twente and Certi_ed Secure, 2012.
[6]D. Wicks, “What is Cydia and Cydia Basics,” IEEnews, Jul. 2016.
[7]J. Golson, “Apple’s App Store now has over 2 million apps,” The Verge, 13-Jun-2016. [Online]. Available: http://www.theverge.com/2016/6/13/11922926/apple-apps-2-million-wwdc-2016. [Accessed: 29-Jan-2017].
[8]O. Raymundo, “Apple is approving apps for the iOS App Store much faster now,” Macworld, 12-May-2016. [Online]. Available: http://www.macworld.com/article/3070012/ios/apple-is-approving-apps-for-the-ios-app-store-much-faster-now.html. [Accessed: 28-Jan-2017].
[9]C. Lloyd, “How Jailbreaking Makes Your iPhone More Secure & Private,” GottaBeMobile, 22-Oct-2015. [Online]. Available: http://www.gottabemobile.com/how-jailbreaking-makes-your-iphone-more-secure-private/. [Accessed: 03-Feb-2017].